Frost & Sullivan Report: Continuous DDoS Vulnerability Testing is Key

Ensure robust DDoS protection with continuous, automated vulnerability testing, as highlighted in Frost & Sullivan’s latest report. Learn why proactive testing is essential to mitigating the evolving threat of DDoS attacks.
Massive DDoS Attack Disrupts X (formerly Twitter) During Trump Interview
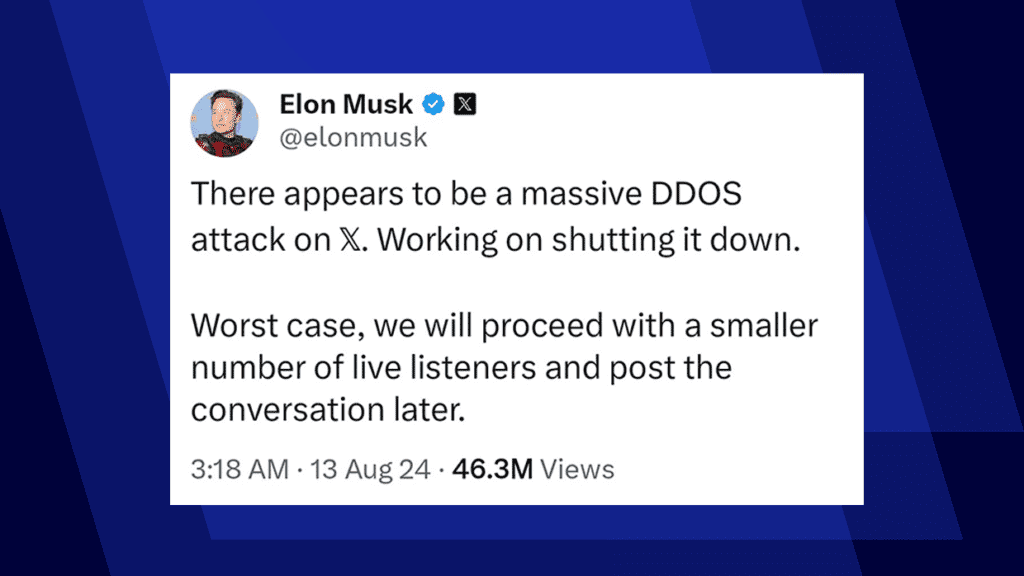
This blog covers the massive DDoS attack that disrupted X (formerly Twitter) during an interview with Elon Musk and Donald Trump, emphasizing the need for stronger DDoS protection and proactive defense strategies.
4 Steps to Compliance and DDoS Resilience

How to be compliant with new DDoS regulations in SEC rulings in the US, and with the Digital Operational Resilience Act (DORA) and NIS 2 Directive in the EU
Don’t Let DDoS Stop the Elections

As the 2024 US national elections approach, the stakes are high – with potential cyber threats posing significant risks to the democratic process.
SEC and DORA Shift the Industry to Proactive DDoS Mitigation – Webinar Recap

Why is it so hard to protect organizations from the Distributed Denial of Service (DDoS) attacks that can impact the business continuity of critical online services? How do the recent cybersecurity rulings of the SEC and new Digital Operational Resilience Act (DORA) regulations in Europe impact the decision-making of the C-suite? And for those organizations […]
8 Things to Check before Choosing Your DDoS Protection

Distributed Denial-of-Service (DDoS) attacks surged this year, according to recent reports. DDoS attacks can overwhelm a network, disrupt services, and cause significant financial and reputational damage. But with a wide range of DDoS protection solutions available on the market, it can be hard to identify which is the best one to meet your organization’s needs. […]
Akamai’s Latest DDoS Report: “Fighting the Heat, EMEA’s Rising DDoS Threats”
Akamai just released a new DDoS report, “Fighting the Heat, EMEA’s Rising DDoS Threats”. The report identifies and highlights the critical need to continuously identify and remediate vulnerabilities in deployed DDoS defenses. This pre-attack approach is a welcome and dramatic shift. This report seems to show that Akamai appreciates the need to shift its focus […]
Understanding DDoS Vulnerabilities
DDoS Attacks Can Only Occur When A Network is Vulnerable. Constantly Reviewing How Your Network is Vulnerable to Different DDoS Attack Vectors is the Only Way To Become Protected
6 Months Until DORA Regulations Kick In. Are You Ready?
DDoS attacks increased in Europe by 73 percent this year – and in 50 percent of the cases, financial services companies were the target. With this steep rise in DDoS attacks, what can financial services organizations do to achieve business continuity? And how does this relate to the EU’s new Digital Operational Resilience Act (DORA)? […]
MazeBolt RADAR™ DDoS Testing is now available in Microsoft Azure

At MazeBolt, our mission is to identify and enable remediation of all DDoS vulnerabilities ahead of time. We’re excited to announce our collaboration with Microsoft Azure, giving our mutual customers the ability to use non-disruptive DDoS testing for the first time. This adds a new level of visibility and enables increased protection on Microsoft Azure. […]
5 DDoS Attacks That Your DDoS Mitigation May Not Prevent

In Q2 2023, there were 44,000 DDoS attacks every single day, a 31% increase on 2022. DDoS attacks are designed to overwhelm a network with traffic, disrupting service or shutting down access to legitimate traffic, and impacting not just the target organization, but its customers, partners, and other stakeholders, too. To meet the growing risk […]
Put Business Continuity First with Continuous Threat Exposure Management (CTEM)
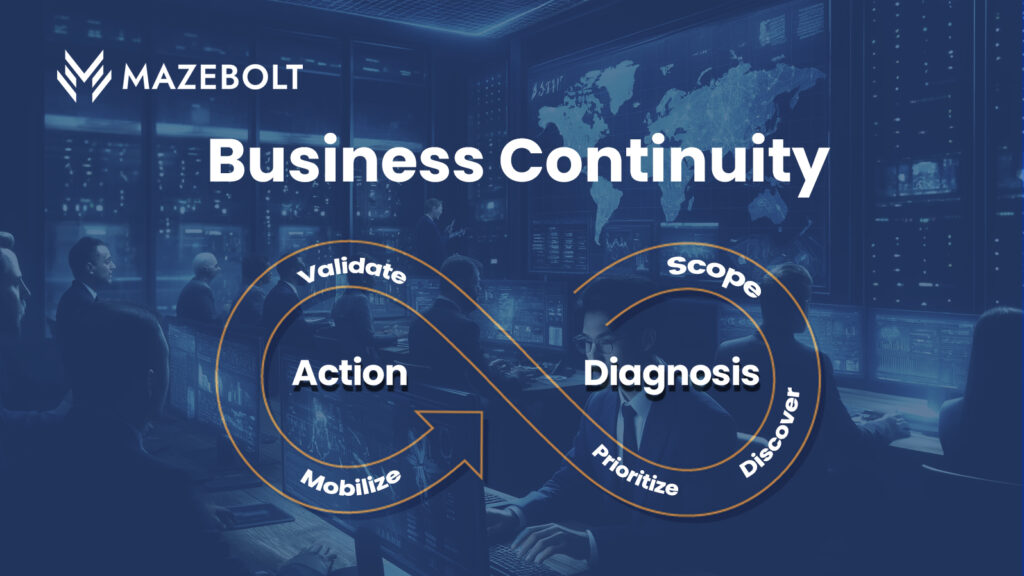
“By 2026, organizations that prioritize their security investments based on a continuous exposure management program will be 3x less likely to suffer a breach.” Gartner’s CTEM framework highlights the need for a Continuous Threat Exposure Management (CTEM) program that acts proactively to surface cyber vulnerabilities and risk and to prioritize issues that are most likely […]
