“By 2026, organizations that prioritize their security investments based on a continuous exposure management program will be 3x less likely to suffer a breach.” Gartner’s CTEM framework highlights the need for a Continuous Threat Exposure Management (CTEM) program that acts proactively to surface cyber vulnerabilities and risk and to prioritize issues that are most likely to impact business continuity and cyber resilience.
In 2023, researchers noted a 200% increase in DDoS attacks, highlighting a critical area of concern for security leaders in today’s digital ecosystem. Not only do DDoS attacks disrupt business continuity, they can result in significant financial losses as well as devastating reputational harm. By aligning proactive risk assessment of DDoS attacks with the CTEM framework, organizations can bolster the management and mitigation of DDoS threats in line with industry best practices.
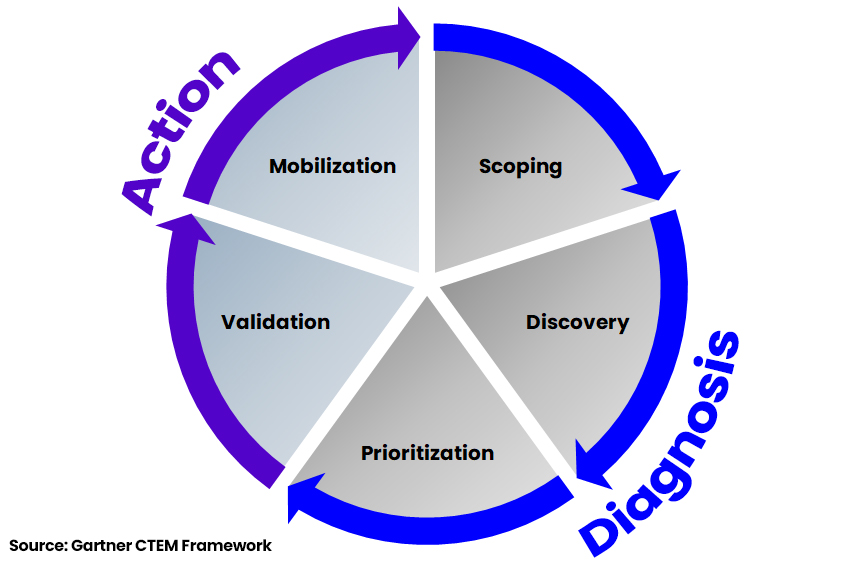
How Does “CTEM” Work?
There are five steps in the CTEM framework, split across two categories – Diagnosis and Action.
At the diagnosis stage, organizations Scope their attack surface, Discover all assets and their risk profiles, and Prioritize the threats that are most likely to be exploited, based on considerations such as the risk level to the organization.
Then, to take action, teams should Validate whether attackers could take advantage of these threats, and Mobilize teams to operationalize CTEM findings to mitigate business risk.
For DDoS risk assessment, organizations often hit a visibility wall. Once a DDoS protection solution has been deployed, and configured as “always on”, how can security leaders be sure that the solution is effective at ensuring vulnerabilities do not emerge that expose their organization to attacks?
While CTEM advocates for the continuous identification of vulnerabilities within the network infrastructure, and highlights proactive mitigation rather than reactive measures, without detailed insight into the effectiveness of existing DDoS protections, data-driven evaluation of cyber resilience is impossible.
CTEM Alignment Demands Continuous DDoS Testing
To diagnose risk across a complex network infrastructure in line with CTEM principles, organizations need an approach to vulnerability testing that proactively looks for gaps or weaknesses in current DDoS protections. Of course, to ensure no business disruption, this has to occur without downtime to live environments.
An intelligent, automated DDoS testing solution checks both boxes. First, it aligns with CTEM by offering continuous scanning and testing across the network and application layers to uncover any vulnerabilities in existing DDoS protection solutions. At the same time, it acts non-disruptively so that there is no impact to business continuity. As vulnerabilities are identified ahead of time, organizations can Scope, Discover and Prioritize the risk levels according to their contextual CTEM framework, long before they can be exploited by threat actors.
This approach allows security leaders to align with CTEM’s focus on proactive threat mitigation. As DDoS attacks are simulated in a controlled manner, organizations can fully understand their exposure, with no risk to critical business assets, and strengthen their cyber resilience ahead of time.
Once threats have been scoped, discovered, and prioritized, the next stage in the CTEM cycle is validation and mobilization. Without continuous and automated DDoS vulnerability testing, security teams can’t evaluate the effectiveness of current DDoS protection solutions, or prepare ahead of time to mitigate and reduce the business impact of identified vulnerabilities. However, with an automated solution in place, your security team will receive detailed insights and analytics on the potential impact of DDoS attacks and validate how effective your current solutions are at stopping them in their tracks after mitigation steps have been completed. With a data-driven approach, organizations can prioritize their remediation efforts based on the severity and the potential impact of an attack, exactly as recommended when following CTEM principles.
MazeBolt RADAR™: Continuous DDoS Testing to Ensure Business Continuity
CTEM is one of Gartner’s top strategic technology trends for 2024, and 60% of organizations are already actively pursuing or are planning to implement a CTEM framework. DDoS attacks are too significant a risk, with too great a potential business impact to leave out of your CTEM strategy.
MazeBolt’s RADAR™ is a significant advancement in proactively managing the risk of DDoS attacks and works in line with Gartner’s CTEM framework. With RADAR, organizations can test continuously across all online services and all known attack vectors without dealing with any disruption or downtime. DDoS protection solutions are put through their paces, and any vulnerabilities are flagged immediately alongside the recommended steps for mitigation. As you have the ability to test continuously, after mobilization your teams have the instant validation that the problem has been resolved. This meets the CTEM guidelines for continuous testing, proactive mitigation, and data-driven evaluation.
Any solutions that support CTEM need to become part of business-as-usual, and that’s exactly how MazeBolt’s RADAR is designed, complementing and enhancing any organization’s existing security measures in an agnostic way. RADAR starts by addressing the immediate challenge of DDoS vulnerabilities, but then takes it a step further by contributing to the broader objective of enhancing organizational cyber resilience and ensuring business continuity.
By providing automated testing, alongside actionable insights and recommendations, RADAR fine-tunes the overall security posture, ensuring DDoS defense is accurate, robust and resilient.
Interested in implementing automated DDoS protection that’s fully aligned with CTEM principles? Reach out to MazeBolt.