Over 13 million DDoS attacks were observed last year, according to a recent NetScout report. The average impact of a damaging DDoS attack is $400,000. This growing number of DDoS attacks – and their incredible cost – begs the question: How does DDoS work? And how can the risk of these attacks be reduced effectively?
Unlike other types of cyber-attacks, the only way a DDoS attack can succeed in damaging online service availability is through a DDoS vulnerability in the protections deployed. Typically, vulnerabilities arise from the misconfiguration of DDoS protection security policies.
A Case in Point: Web Application Firewall (WAF) vs. DDoS Security
From a theoretical perspective, there should be no need for a WAF if a Web application is continuously validated pre- and post- deployment, and follows an ongoing process of checking for vulnerabilities that includes:
- Undergoing strict static/dynamic application security testing
- Deploying a secure Software Development Life Cycle (SDLC)
- Running regular penetration tests
- Scanning for vulnerabilities
- Applying patches immediately
If this process were followed – theoretically speaking – there would be zero errors in the coding (CVEs/proprietary) or in the logic of the web application that could be exploited, and a WAF would be completely unnecessary.
But this is not the case for DDoS. The only possible protection against a DDoS attack is provided via DDoS mitigation. Unlike a WAF, there is no software engineering on the end service (as described in the example above) that could prevent a DDoS attack from taking down online services.
When it comes to DDoS, organizations are fully reliant on automated DDoS protection solutions for damage prevention. If the solution your organization is using doesn’t work – a DDoS attack will succeed.
Where Are DDoS Vulnerabilities Located?
DDoS vulnerabilities are located within an organization’s DDoS protection solutions – mostly, in the particular solutions’ security policies.
An organization can only suffer a damaging DDoS attack if its DDoS protection is vulnerable. If a DDoS attack penetrates a vulnerability in the deployed DDoS defenses, it’s the customer who suffers damaging downtime. (Note: If a DDoS solution provider goes down, e.g. AWS, Akamai, Microsoft, Radware, Cloudflare, F5, etc., this is considered a force majeure event.)
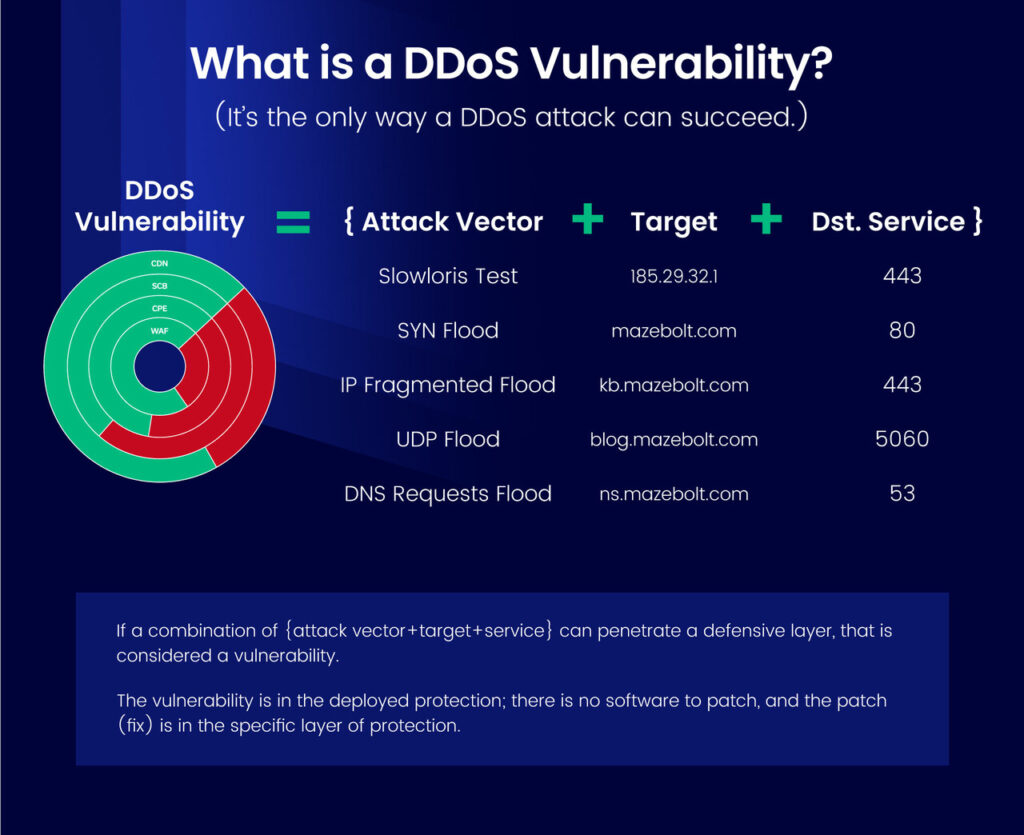
Classifying a DDoS Vulnerability
A DDoS vulnerability can be any combination of the following, assuming it penetrates any of the DDoS protection solutions that have been deployed:
{Attack vector + Target (IP or FQDN) + service port}
The following is one example of a potential DDoS vulnerability:
SYN Flood + example.com + 443
If an attacker launched the above combination against the target example.com:
- The target is classified as protected to the particular attack vector and service combination, if the target’s protection solution automatically blocks the attack (the SYN Flood).
- The target is classified as vulnerable to the particular attack vector service combination, if the target’s protection solution does NOT automatically block the attack (the SYN flood), in which case manual intervention would be required.
Stated differently, the results of the attack will be one of these two options:
Associating DDoS Vulnerabilities with Specific Protection Layers
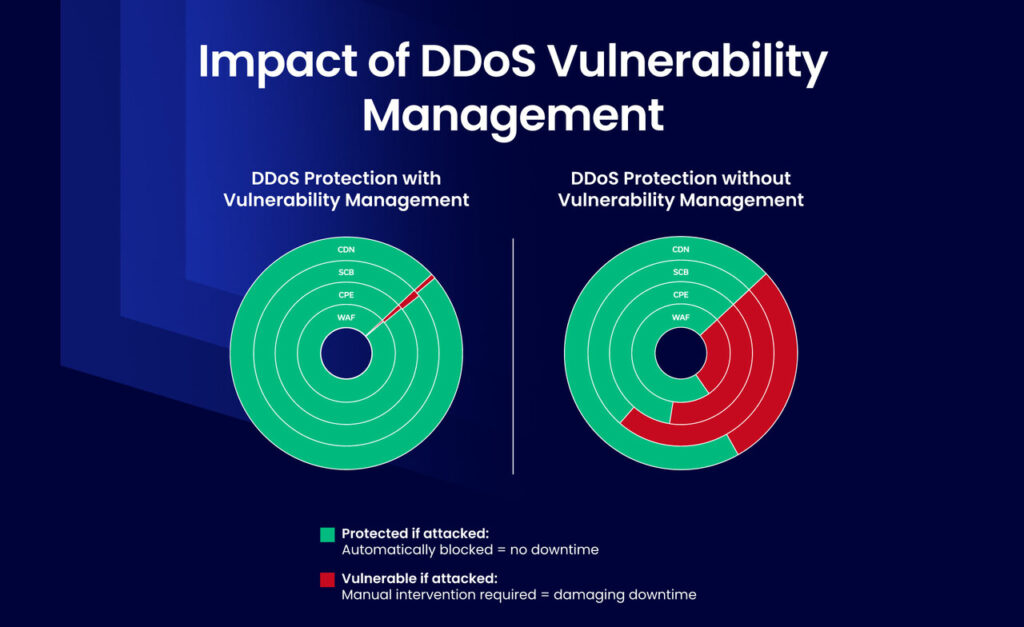
Effective DDoS protection requires multiple (hybrid) layers of protection. Associating a DDoS vulnerability with the relevant protection layer is critical for successful remediation as vulnerabilities can only be remediated in the relevant protection policy.
Where there is just a single layer of protection, e.g., the scrubbing center, it is obvious where the vulnerability is located – as it will be in the scrubbing center itself. However, many organizations have on-premises data centers and cloud deployments, and all are governed by multiple DDoS security layers: scrubbing, WAF, cloud WAF, etc. If there is more than one layer of DDoS protection, it is important to identify in which layer the DDoS vulnerability resides. For example:
SYN Flood + example.com + 443
Scrubbing=vulnerable | On-prem.=protected | WAF=protected
In the above example, the SYN flood penetrated the vulnerability in the scrubbing center security policy, but the on-premises WAF mitigated it. This information allows decision-makers to decide where to focus remediation efforts for this specific vulnerability, i.e., in this particular example it makes sense to remediate the SYN flood to port 443 on the scrubbing center.
If the vulnerability is not patched – and this combination arrives – the target (or even the entire IT infrastructure) is likely to be taken down, until there is manual intervention.
How are DDoS Vulnerabilities Patched?
Patching a DDoS vulnerability in the protection device or service may require multiple adjustments until the mitigations are able to stop the attack automatically. These adjustments may include:
- Changing configurations
- Applying new policies
- Enabling different measures or mechanisms
- Changing rate values
The best way to minimize DDoS vulnerabilities involves continuously testing your organization’s automated DDoS protections, fixing misconfigurations, and re-validating that those vulnerabilities have not returned.
Through the continuous validation of your mitigation devices and services, you can ensure that your organization has the best DDoS protection – reducing the risk of a successful attack.
DDoS Vulnerability Management Can Fully Protect Your Organization from DDoS Attacks
DDoS vulnerabilities differ from other types of vulnerabilities in several important ways:
- DDoS security relies on automated DDoS protection to avoid a damaging DDoS attack
- The only reason a DDoS attack succeeds is when the automated DDoS protection has a vulnerability
- Vulnerabilities typically arise from DDoS protection security policy misconfigurations
- DDoS vulnerabilities exist in the DDoS protection policies, unlike CVEs or proprietary software bugs; the only place to remediate a DDoS vulnerability is in the specific organization’s DDoS protection solution(s)
- Mapping each DDoS vulnerability to each security layer and solution allows for efficient remediation
Interested learning more about DDoS Vulnerability Management? Speak with an expert today!