Blog
The IT Guide to DDoS: ISO Layer 7 – What You Need to Know (Part 3)
Explore how Layer 7 DDoS attacks target application resources, mimicking normal traffic to bypass defenses and cause disruptions. Learn about attack types, their impact, and effective mitigation strategies to safeguard applications and services. Read more
The IT Guide to DDoS: ISO Layer 7 – What You Need to Know (Part 3)
Explore how Layer 7 DDoS attacks target application resources, mimicking normal traffic to bypass defenses and cause disruptions. Learn about attack types, their impact, and effective mitigation strategies to safeguard applications and services.

Frost & Sullivan Report: Continuous DDoS Vulnerability Testing is Key
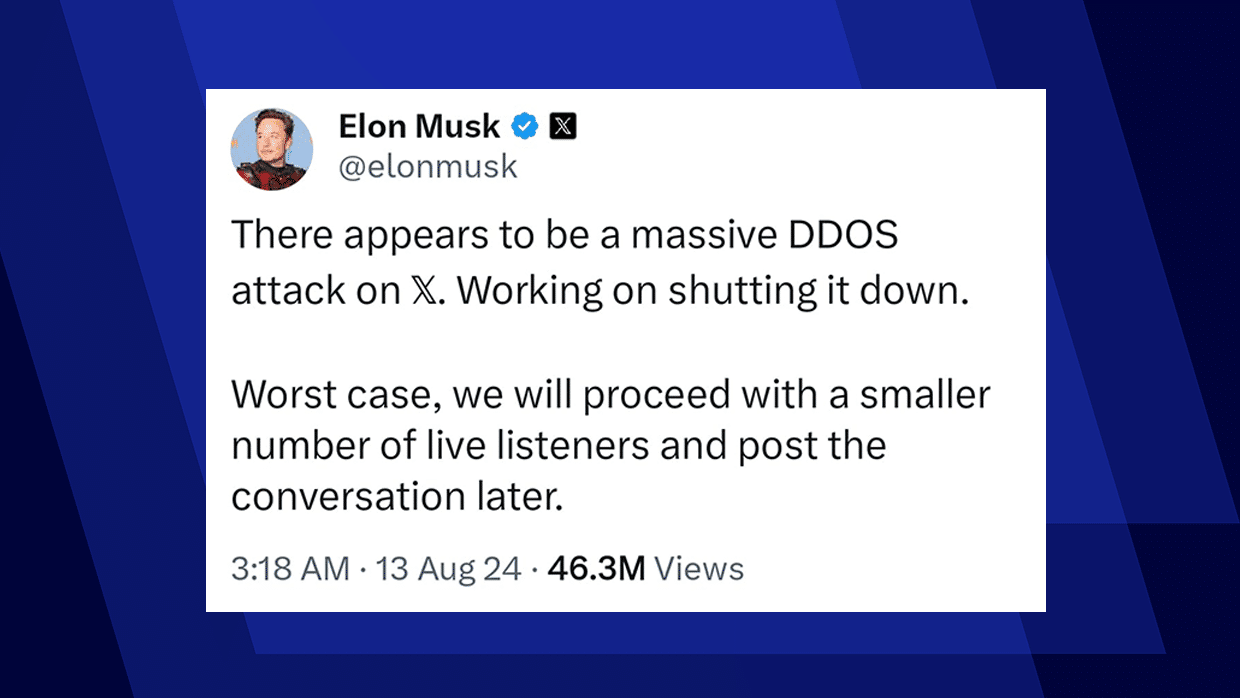
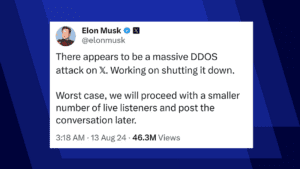
Massive DDoS Attack Disrupts X (formerly Twitter) During Trump Interview

4 Steps to Compliance and DDoS Resilience
Don’t Let DDoS Stop the Elections
SEC and DORA Shift the Industry to Proactive DDoS Mitigation – Webinar Recap

8 Things to Check before Choosing Your DDoS Protection
Akamai’s Latest DDoS Report: “Fighting the Heat, EMEA’s Rising DDoS Threats”