Yesterday, August 12, 2024, the X platform (formerly Twitter) experienced a significant Distributed Denial-of-Service (DDoS) attack. This attack coincided with the highly anticipated interview between Elon Musk and former President Donald Trump, causing substantial delays and disruptions.
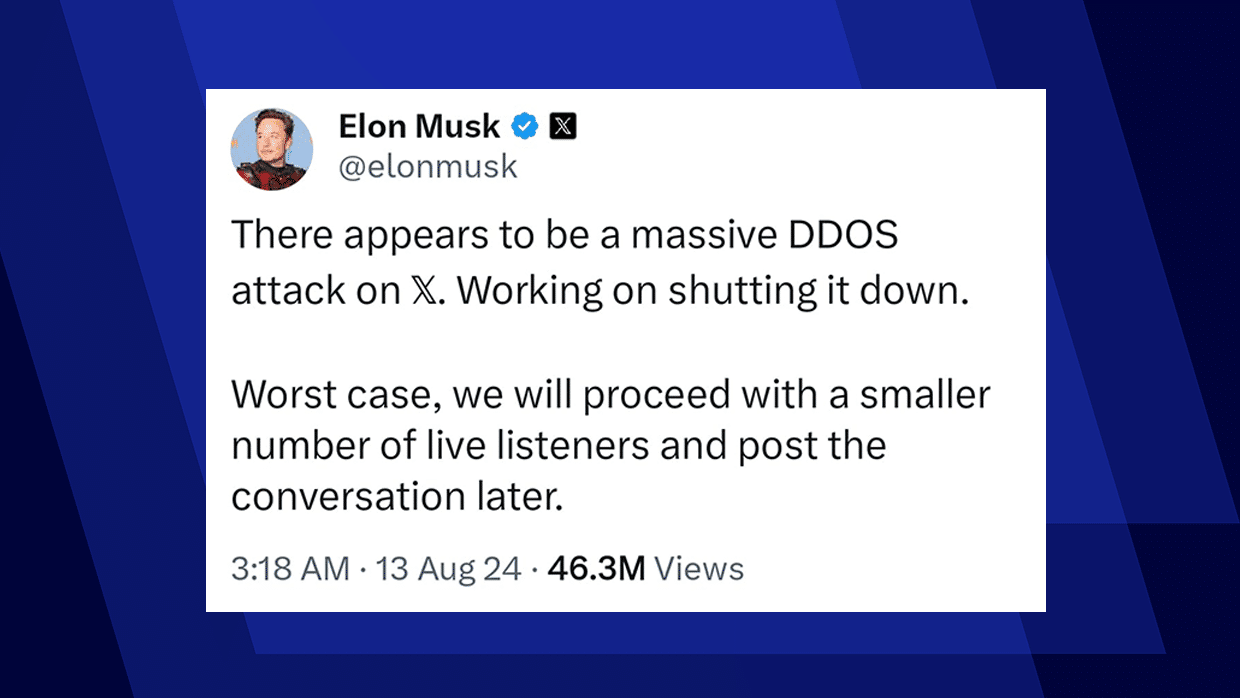
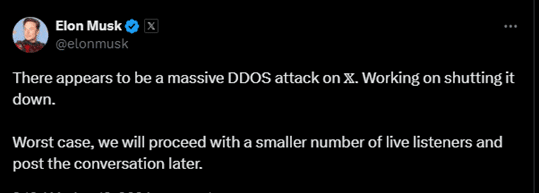
The DDoS attack began around 8 p.m. ET, just as the interview was scheduled to start. Users attempting to join the live stream reported being unable to access the platform, receiving error messages or timeouts instead. Elon Musk quickly took to the platform to inform users about the situation, stating, “There appears to be a massive DDoS attack on X. Working on shutting it down. Worst case, we will proceed with a smaller number of live listeners and post the conversation later.”
Trump’s team posted that the “interview on X is being overwhelmed with listeners logging in.”
Despite the technical difficulties, the interview eventually commenced around 8:40 p.m. ET, with less than 1 million listeners tuning in. While the attack wasn’t fully mitigated, the interview continued. Eventually, the platform was able to sustain 8 million concurrent listeners – well under the expected crowd. Coincidentally, Musk said prior to the broadcast that X had tested the system “with 8 million concurrent listeners earlier today.” It is not clear when the attack ended, though there are some indications that the issues ended as soon as the interview was over.
A More In-Depth Look at This DDoS Attack
A DDoS attack involves overwhelming a target server with a flood of internet traffic, rendering it unable to function properly. These attacks are typically orchestrated using a network of compromised computers which simultaneously send a massive number of requests to the target server. The goal is to overwhelm the service’s resources, causing it to slow down or crash.
In this case, the DDoS attack on X was significant enough to disrupt the platform’s services for over 45 minutes. The attack’s scale and timing suggest a coordinated effort, possibly by a group with substantial resources and technical expertise.
While the exact perpetrators of the attack remain unidentified, some reports suggest that a hacking group known as Anonymous Sudan may be behind it. This group has previously targeted X and other organizations to pressure Elon Musk into launching his Starlink service in different locations. Despite their name, Anonymous Sudan operates mostly from Russia and is managed by a network of cybercriminals. Initially claiming Sudanese origins, the group’s affiliation with Russia is pretty clear and is linked to the Russian backed group KillNet.
In Response to the Attack
The implications of such attacks are far-reaching. For X, the immediate impact was the disruption of a high-profile event, potentially affecting user trust and platform reliability. For users, it highlighted the vulnerability of even the most prominent social media platforms to cyber threats.
In response to the attack, X’s technical team worked to mitigate the impact and restore normal operations after the attack already began. This involved identifying and blocking malicious traffic, changing configurations in real time, reinforcing server defences, and ensuring that legitimate users could access the platform.
This could all have been prevented had the automatic defenses been properly configured, tested, and prepared for such attacks. To prevent future incidents, X may need to invest in advanced DDoS protection and testing solutions.
The Need for Proactive DDoS Vulnerability Identification and Remediation
Adequate preparation in the age of automatic DDoS protection and mitigation requires continuously identifying and remediating vulnerabilities in deployed DDoS defenses. Instead of reacting in real time, and suffering the consequences of disruption or downtime, like the technical teams at X, proactive vulnerability identification and remediation would have stopped the attack before it began.
The DDoS attack on X serves as another reminder of the ever-present DDoS threat facing online platforms. It underscores the importance of robust protection and identification measures and the need for constant vigilance to protect online services and their users.
To learn more about proactive DDoS Vulnerability Identification and Remediation, click here.