Introduction
On September 8, 2019 online players of the epic World of Warcraft game from Blizzard, were very mad. They were having many problems with the game, some were dropping off, some unable to log into and some even incurred penalties if disconnected from competitive modes. After three hours of latency, more than a 1000 tweets from angry fans rained on Blizzard, dissatisfied players vented out their frustrations online. While the IT team at Blizzard kept updating its fans, it was still 48 hours before they could bring back the site to normal status.
Just two days before this attack, Wikipedia suffered what appears to be the most disruptive Distributed Denial of Service (DDoS) attack in recent memory. Historically, Wikipedia had been attacked a couple of times , but this time it was different. The attack was far larger and went on for nearly 3 days. The site became unavailable in Europe, Africa, and the Middle East, and slowed down for users in the US and Asia.
Attacks like the ones mentioned above are not rare. In fact, last year, over 8.4 million attacks occurred. That amounts to 23000 attacks every day, i.e. 16 every minute. The average cost of an attack starts from $50,000/- moving upwards. Not to mention loss of productivity, customer trust and competitive disadvantage. In a recent survey, 78% security professionals said that the most damaging effect of DDoS attacks on businesses was customer confidence and trust.
Why attacks are increasing
The number of attacks have grown significantly across industry segments and business sizes. There was a 168% increase in distributed denial-of-service (DDoS) attacks in Q4′ 19, compared with Q4’18, and a 180% increase overall in 2019 compared to 2018. The reason for this alarming rise in attacks could be the easy availability of DDoS-for-hire in the dark web, making it so much easier and cost effective for perpetrators to cause damage to enterprises by launching malicious attacks. There are other reasons too. Some attacks are launched by `hactivists’, targeting ideologically different businesses. Also, business feuds are fairly often cited as a reason for launching DDoS attacks. There are people who are so bored that launching an attack gives them an adrenaline rush. But the simplest motive is money, as attacks are launched to extort money.
How Confident are you about your DDoS Mitigation efficiency?
To prevent attacks, enterprises, both small and large have likely invested in one or the other mitigation solutions highlighted below:
- Scrubbing Center (BGP)
- Content Delivery Network (CDN)
- Vendor Appliances (CPE Equipment)
- Intrusion Detection System/Intrusion Prevention System
- Web Application Firewall
There are generally three types of DDoS mitigation postures:
- Cloud based,
- On-Prem solutions,
- Hybrid combinations of the two.
The table below shows different DDoS mitigation postures and their capabilities to mitigate DDoS attacks:
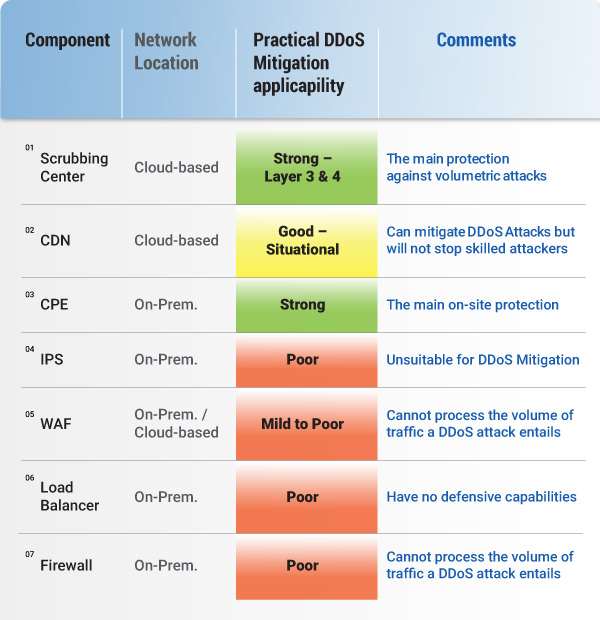
From the above analysis it is obvious that no single DDoS Mitigation Posture is comprehensive. It is also apparent that today’s DDoS mitigation is missing the critical functionality, to be able to continuously identify and fix vulnerabilities generated due to the underlying network changes.
About RADAR™
RADAR™, MazeBolt’s new patented technology solution is part of the MazeBolt security platform. RADAR™, simulates DDoS attacks continuously and non-disruptively. Delivering advanced intelligence, through straightforward reports on how to remediate the DDoS vulnerabilities found.
Closing the DDoS gap by assisting your mitigation solution to fix ongoing security gaps before they are exploited. Using RADAR™ you never have to rely on risky zero-day reactive mitigation capabilities.
RADAR™ assists organizations in achieving, maintaining, and verifying the continuous closing of their DDoS vulnerability gaps. Reducing and maintaining the vulnerability level from an average of 48% to under 2% ongoing.
About MazeBolt
MazeBolt is an innovation leader in cybersecurity and part of the DDoS mitigation space. Offering full DDoS risk detection and elimination and working with any mitigation system to provide end to end full coverage. Supporting organizations in avoiding downtime and closing DDoS vulnerabilities before an attack happens.