This post is part of a series about Layer 3, Layer 4, and Layer 7 DDoS attacks.
Layer 4 DDoS attacks are particularly dangerous because they focus on overloading the transport layer protocols – without necessarily needing to consume vast amounts of bandwidth. Layer 4 attacks target the transport layer in the Open Systems Interconnection (OSI) model.
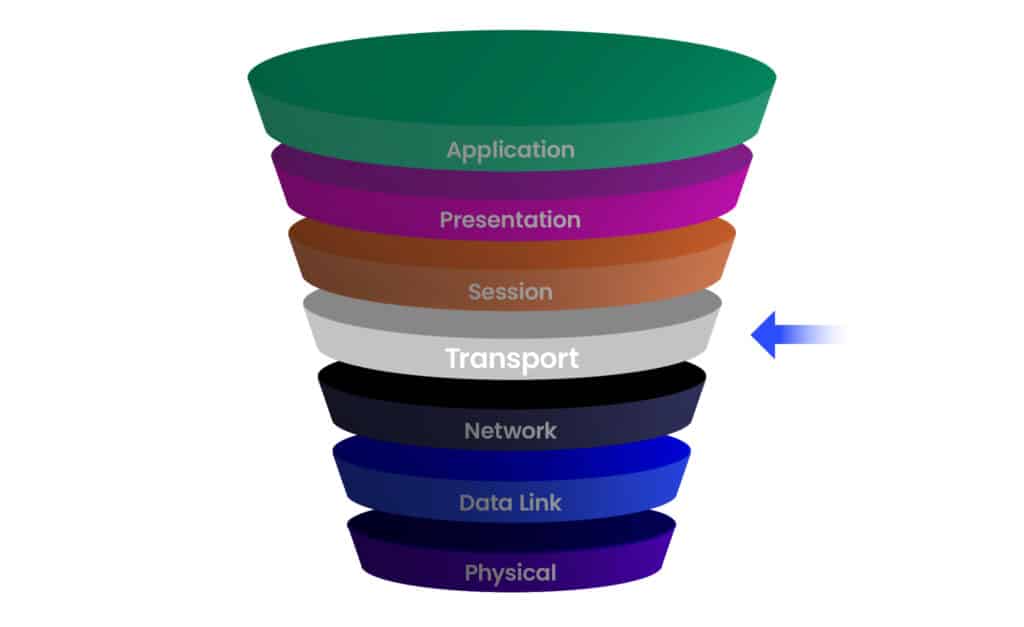
Layer 4 of the OSI Model: One of the Key Targets for DDoS Attacks
Layer 4 DDoS attacks disrupt the communication protocols responsible for data transfer between systems. They enable attackers to cause significant disruption using relatively small amounts of traffic – by exploiting vulnerabilities in TCP/UDP connections. Compare this to Layer 3 (network layer) DDoS attacks, which involve sending vast amounts of traffic simultaneously. Here’s how they work:
Exploiting Protocols that are Essential for Communication
Layer 4 DDoS attacks aim to exploit vulnerabilities in protocols that are vital for establishing connections between devices on a network, including:
- Transmission Control Protocol (TCP): Provides reliable, ordered, and error-checked delivery of data
- User Datagram Protocol (UDP): Delivers data without verifying its reception; a connectionless protocol, it is often used for real-time applications like video streaming
SYN Floods
SYN floods are one of the most common types of Layer 4 DDoS attack. SYN floods target the TCP handshake, which is also known as a three message handshake or SYN-SYN-ACK. Here’s how SYN floods work:
- When a client initiates a connection with a server, it sends a SYN (i.e., synchronize) packet to begin the three-way handshake.
- The server responds with a SYN-ACK (synchronize-acknowledgment) packet
- In a SYN flood attack, the attacker either sends no ACK (acknowledgment) in response or sends a flood of SYN requests. This leaves many half-open connections on the server, which exhausts server resources and prevents legitimate users from establishing connections.
UDP Floods
UDP floods are another type of Layer 4 DDoS attack. In a UDP flood, the attacker sends a large number of UDP packets to random ports on a target server.
Since UDP is connectionless, the target server must respond with ICMP “destination unreachable” messages if no application is listening on the port. This wastes bandwidth and processing power, leading to service disruption.
ACK Floods
ACK floods are a type of Layer 4 DDoS attack that floods a target server with TCP ACK packets, overwhelming its ability to process these acknowledgments.
ACK floods target the server’s ability to manage its resources by sending an unusually large number of ACK packets, often causing server overload and downtime.
Two Ways that Layer 4 Attacks Can Affect Your Online Services
DDoS attacks can exhaust the server’s capacity to manage connection state or overwhelm the bandwidth or computing resources of the network.
1. Exhausting the Server’s Capacity to Manage Connection States
One of the primary features of Layer 4 DDoS attacks is that they attempt to exhaust the server’s capacity to manage connection states – i.e., bringing them to connection state overload.
In TCP-based attacks like SYN floods, for example, the server allocates memory and resources for each connection attempt. If the attacker initiates a large number of fake connections, the server quickly runs out of resources, causing it to slow down or crash.
As a result, the server can end up in a compromised position with:
- Half-open connections: With SYN floods, many connections remain in a half-open state, consuming resources without being completed.
- Overloaded connection tables: Routers and firewalls that track connection states can also be overwhelmed by Layer 4 DDoS attacks, as they have finite space for tracking these connections.
2. Overwhelming the Bandwidth or Computing Resources of the Target’s Network
Layer 4 DDoS attacks often rely on bringing the target network to a state of bandwidth and resource exhaustion. The goal is to send a flood of packets (whether SYN, UDP, or ACK packets) at a rate that exceeds the target’s capacity to process them. This can lead to:
- Bandwidth saturation: The network bandwidth is fully consumed, preventing legitimate traffic from reaching the server.
- Server resource exhaustion: The target’s CPU, memory, and other resources are overwhelmed by the sheer volume of traffic.
Amplification Techniques Involving an Intermediary Server
Attackers sometimes use amplification techniques in Layer 4 attacks, especially in UDP reflection/amplification attacks. In these attacks, the attacker sends small requests to an intermediary server that responds with a much larger reply, which is then directed toward the target (victim).
Examples include DNS amplification or NTP amplification attacks. This approach allows attackers to greatly increase the volume of traffic directed at the victim while using minimal resources.
How to Mitigate Layer 4 DDoS Attacks
Methods of mitigating Layer 4 DDoS attacks include:
- SYN cookies: A technique where the server sends back minimal state information with its SYN-ACK response, only allocating resources when the client responds with the correct ACK.
- Rate limiting: Limiting the number of TCP/UDP requests a server will process per second can reduce the impact of an attack.
- Stateful firewalls and Intrusion Prevention Systems (IPS): These can detect abnormal traffic patterns (like a flood of SYN or UDP packets) and filter out malicious traffic.
- DDoS mitigation solutions: Specialized DDoS protection solutions can reroute traffic through scrubbing centers that filter out malicious traffic and allow legitimate traffic to pass through.
Continuous DDoS Vulnerability Testing Enables the Proactive Elimination of DDoS Attacks
Unlike other types of cyber attacks, the only way DDoS attacks can succeed in creating damaging downtime is via a DDoS vulnerability in the DDoS protections deployed. Vulnerabilities tend to arise from misconfigurations in DDoS protection security policies that bring down online services.
The best way to minimize DDoS vulnerabilities involves continuously testing your organization’s DDoS protections, monitoring for and fixing misconfigurations, and re-validating that those vulnerabilities have not returned.
MazeBolt RADAR™ is a DDoS vulnerability management solution that runs continuous attack simulations to uncover vulnerabilities that can cause damaging attacks and interrupt business continuity. RADAR provides organizations with the required insights to identify DDoS vulnerabilities proactively and automatically, without downtime. Through continuous validation of DDoS defenses, you can reduce the risk of a successful attack.
To learn more about DDoS Vulnerability Management, speak with a MazeBolt expert.
This is the second post in a series about different types of DDoS attacks. Click here to read the post about Layer 3.