Blog
The IT Guide to DDoS: Layer 4 – Everything You Need to Know (Part 2)
Learn how Layer 4 DDoS attacks target vulnerabilities in transport layer protocols like TCP and UDP to cause significant disruption without requiring vast amounts of traffic. Explore key attack types such as SYN floods, UDP floods, and ACK floods, and how to mitigate these threats.

Insights for Cybersecurity Awareness Month: 3 Tips on DDoS Resilience
The IT Guide to DDoS: Layer 3 – What You Need to Know (Part 1)

Doing Business in the EU? October 17 is the NIS2 Deadline

Frost & Sullivan Report: Continuous DDoS Vulnerability Testing is Key
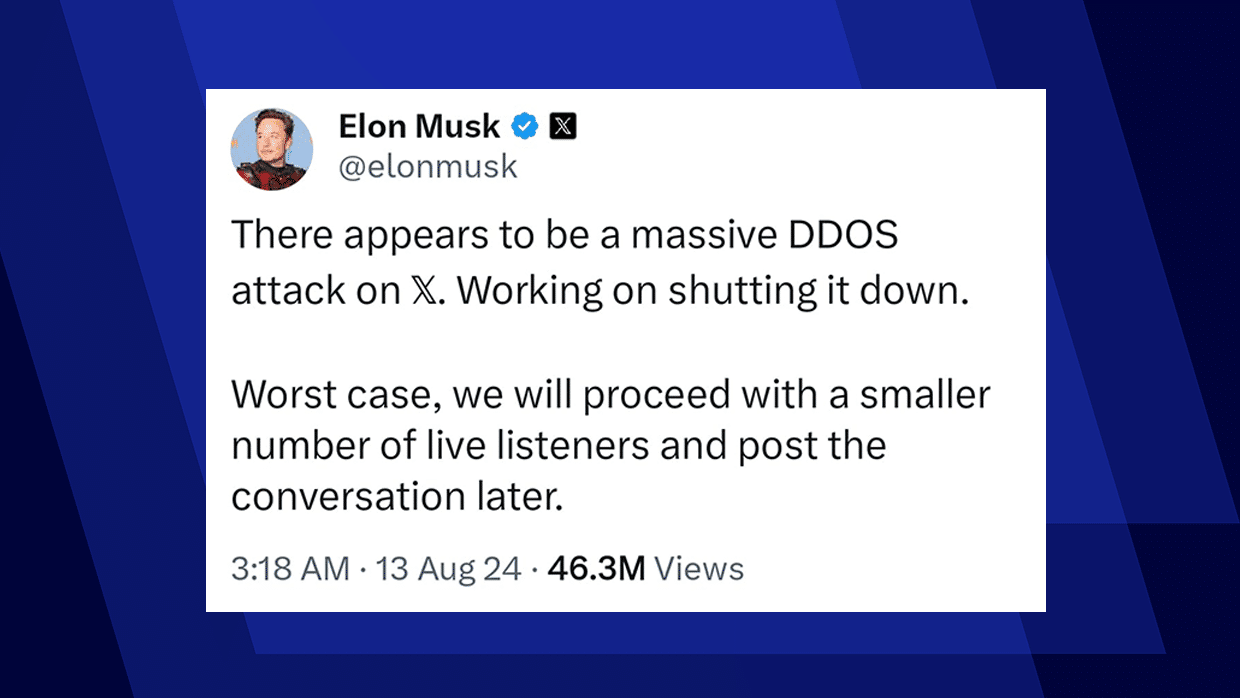
Massive DDoS Attack Disrupts X (formerly Twitter) During Trump Interview

4 Steps to Compliance and DDoS Resilience
Don’t Let DDoS Stop the Elections
SEC and DORA Shift the Industry to Proactive DDoS Mitigation – Webinar Recap

8 Things to Check before Choosing Your DDoS Protection
Akamai’s Latest DDoS Report: “Fighting the Heat, EMEA’s Rising DDoS Threats”

Understanding DDoS Vulnerabilities