Blog
Choosing the Right DDoS Protection: 6 Tips for CISOs
X’s March 2025 DDoS outage exposed major gaps in protection. Learn how to choose the right DDoS vendor and avoid damaging downtime. Read more
Choosing the Right DDoS Protection: 6 Tips for CISOs
X’s March 2025 DDoS outage exposed major gaps in protection. Learn how to choose the right DDoS vendor and avoid damaging downtime.
The Real Reason DDoS Succeeds – And What Your DDoS Protection Is Missing

Leveraging AI to Protect the Largest Attack Surfaces from DDoS: Introducing RADAR SmartCycle™
How DDoS Attacks Unfold: Reactive vs. Proactive Approaches to Defense

Crippling DDoS Attacks Strike Europe – Webinar Recap

2015 in DDoS Attacks – Highlights of noteworthy DDoS attacks in 2015

Trust your DDoS mitigation configuration. No, really.
BVP lists MazeBolt as one of the fastest growing Enterprise Security Startups

DDoS Extortion – Biting the DDoS Bullet
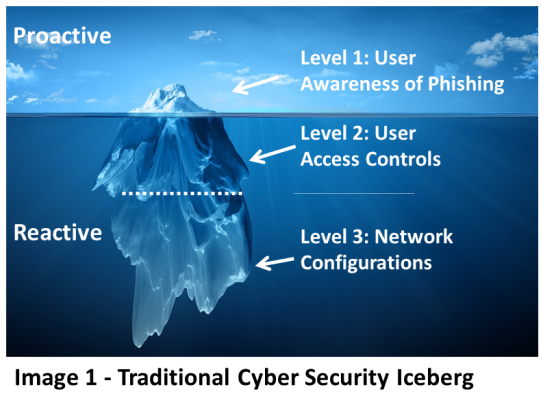
The Cyber Security Iceberg – Which Way Is Up?

The 4 Phishing Commandments – #4 Unshare Thyself

The 4 Phishing Commandments – #3 Know Thy Link