As more and more enterprises interact within their ecosystem through various web and IP-based applications, they become targets for threat actors with malicious intentions. These threat actors launch DDoS attacks to impact businesses and consequently their bottom line. To defend their online presence, maintain employee productivity, and safeguard their infrastructure, organizations rely on DDoS mitigation solutions.
DDoS mitigation usually follows these steps:
-
Identification
Identification A website needs to be able to differentiate between organic high-volume traffic and a distributed attack. For example, if the website has just made a news announcement or an eCommerce site is running a sale, the last thing that is needed is for legit traffic to be treated as suspicious traffic and blocked.
-
Response
Response During an attack, the DDoS protection network identifies incoming threats and drops malicious traffic, making the service available for legit traffic. This can take place by any DDoS mitigation solution such as different security challenges, a drop of identified malicious traffic, or traffic rerouting to multiple resources.
-
Routing
Routing traffic to multiple resources will help to break the traffic into smaller chunks to prevent service denial and finally analyze patterns for future protection.
The DDoS Vulnerability Gap
Even with the most sophisticated DDoS mitigation and testing solutions deployed, most companies are left with a staggering 48% DDoS vulnerability level. The vulnerability gap stems from DDoS mitigation solutions being reactive instead of continuously evaluating and closing vulnerabilities.
DDoS mitigation solutions are not constantly being re-configured and fine-tuned with their DDoS mitigation policies. This leaves organizations with limited visibility to DDoS vulnerabilities, forcing them to troubleshoot issues at the very worst possible time (i.e. when systems are brought down by a successful DDoS attack). These solutions are all reacting to an attack rather than proactively closing DDoS vulnerabilities before an attack happens.
The vulnerability gap occurs when DDoS traffic bypasses a DDoS mitigation defense, accessing the target network and causing systems disruption and online services unavailability.

What if mitigation solutions could detect the vulnerabilities and exposed `attack’ surfaces within the underlying networks they protect?
If service providers could see through the looking glass long before the actual onset of an attack, then the entire approach to mitigation could be different. This is where RADAR™ testing comes in.
RADAR™ testing is always-on, constantly testing, and non-disruptive. It delivers advanced intelligence through straightforward reports on how to remediate the DDoS vulnerabilities found so that you can fix vulnerabilities before they are exploited.
Here are some of the ways RADAR™ testing eliminates the vulnerability gap:
- Automatically validates DDoS mitigation against over 100 DDoS attack vectors on all OSI Layers 3, 4, and 7.
- Identifies areas of weakness and provides in-depth analysis of DDoS weaknesses.
- Reports vulnerabilities in an ongoing manner to allow security teams to close weaknesses and validate configuration changes quickly without disrupting the tested environment.
- Validates that DDoS attacks are automatically mitigated and will not require human intervention at the time of an attack.
- On average, RADAR™ testing constantly tests hundreds of DDoS attacks per month without disruption (maintenance windows are not required).
MazeBolt RADAR testing works together with an organization’s security team and the respective mitigation partners creating easy-to-implement DDoS vulnerability reports, and retesting to verify these vulnerability gaps have been eliminated. RADAR testing is always-on, constantly testing, and non-disruptive to your production environment.
A typical report provides extensive information on all identified vulnerabilities and whether they are fully protected, partially protected, or vulnerable to exploitation under the current DDoS mitigation provider:
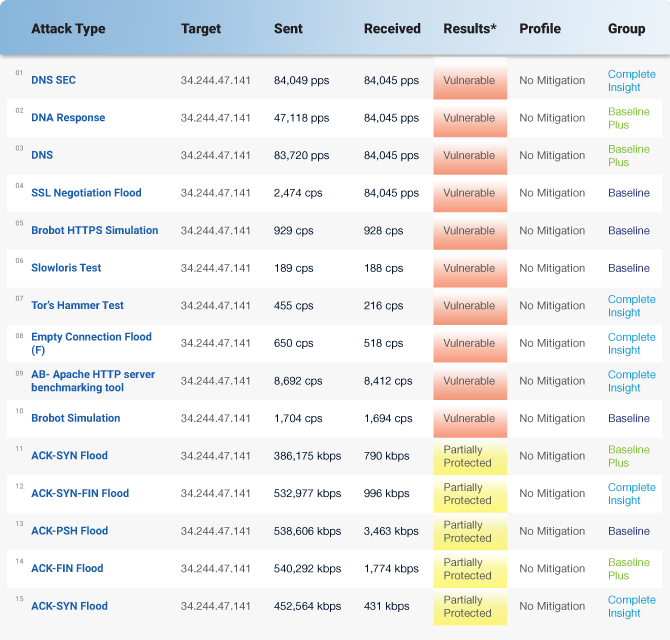
The report also includes screenshots that show the attack and its monitoring:
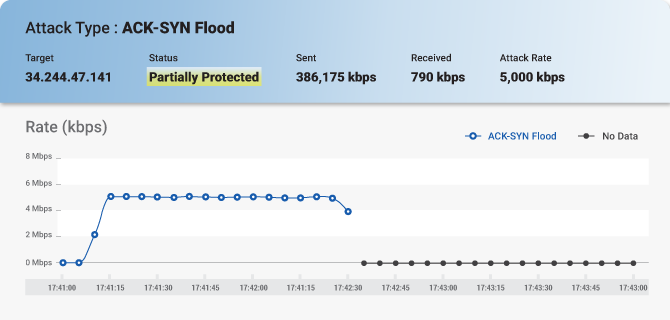
Besides the reports, MazeBolt’s services include experts that are available for mitigation vendors to clarify, explain, and ensure that all vulnerabilities are identified and eliminated. RADAR™ testing alone is also DDoS mitigation agnostic so it works with any existing mitigation solution to ensure your organization’s DDoS risks are eliminated. Organizations can now address DDoS threats before any attack instead of only addressing them during an attack in real-time.