DDoS attackers are improving their arsenal and successfully targeting companies to cause damaging downtime. DDoS attacks are becoming more intense and multimodal, and in some cases taking the shape of demanding ransom. Since the global lockdown onset, organizations are experiencing a massive digital transformation and identifying DDoS vulnerabilities has become more difficult. As a result, DDoS mitigation solutions are having to work harder to mitigate and protect organizations against DDoS attacks.
What is a DDoS Vulnerability Gap?
A DDoS vulnerability gap is the percentage of DDoS attacks that succeed in bypassing a company’s DDoS mitigation defenses and penetrating the target network. For example, if 10 DDoS attacks hit an organization and its mitigation policy blocked only 8 of them, then the DDoS vulnerability gap is 20%.
There are a few factors that contribute to the DDoS vulnerability gap:
Dynamic Business Environments
In the business world, organizations need to quickly grow to keep up with the cut-throat competition. They need to do this while also meeting the latest security requirements, which can be challenging. For example, the recent work-from-home phenomenon that was a result of the global pandemic forced organizations to create last-minute policies to protect themselves.
.In addition, the ongoing digital transformation includes deploying new servers, software, applications, and IT updates every other week. In October 2020, software intelligence company Dynatrace conducted an independent global survey of 700 CIOs to analyze the need for digital transformation; the report reveals that 89% of CIOs say the digital transformation has accelerated in the last 12 months, and 58% predict it will continue to speed up.
During a digital transformation, network vulnerabilities increase and often remain undetected. Vulnerability identification remains a challenge because continuous, 24-7 DDoS testing is expensive and impractical. Despite advanced technology available, mitigation solutions do not have automatic fine-tuning and require manual reconfiguration. Network configurations, on the other hand, are dynamic and change constantly. As a result, the magnitude of the DDoS vulnerability gap increases as organizations embrace digital transformation and make constant changes to their network.
DDoS Attack Vectors Becoming Complex
Another reason contributing to widening the DDoS vulnerability gap is the increase in intensity, complexity, and sophistication of DDoS attack types, making attack detection a challenge.
The NETSCOUT Threat Intelligence Report mentions 4.8 million attacks in the first half of 2020, and confirms that complex 15-plus vector attacks have spiked 126 percent year over year and 2,851 percent since 2017, further complicating mitigation strategies. Another report from NETSCOUT observes more than 10 million DDoS attacks in the year 2020, i.e. nearly 1.6 million more attacks than seen in 2019.
DDoS attack vectors strike networks on three different layers of the OSI model. Attacks hitting different layers have distinct characteristics. DDoS attackers exploit the multi-vector technique within each of these three OSI layers, significantly complicating attack identification and mitigation.
(see Figure 1 for attack characteristics and attack type by OSI layer examples).
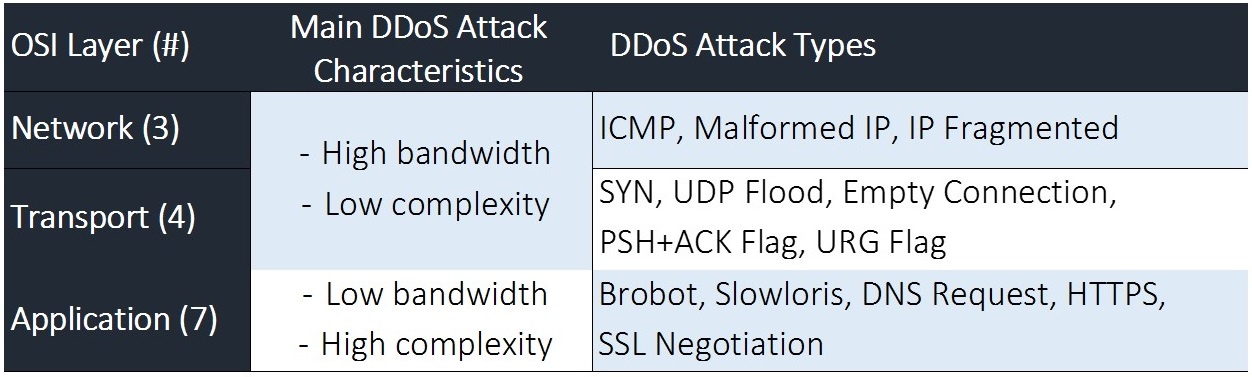
Figure 1
Multi-vector attacks are on the rise because the tactic improves DDoS attackers’ possibilities to damage a network successfully. For example, attackers launch different vectors at once or modify the vectors in response to the mitigation solution. The attack strategy changes every few minutes. That way if one vector fails, the other hits the target network within seconds before mitigation can react. A deployed mitigation solution is configured to block identified vectors; however, it lacks real-time reconfiguration to prevent DDoS vector variations, increasing the DDoS vulnerability gap.
Hybrid Mitigation Solutions are Not Enough
Organizations deploy a combination of DDoS mitigation systems to combat the complexity of DDoS Attacks. Cloud-based Scrubbing centers and Content Distribution Networks (CDN) mitigate high bandwidth Layer 3 and Layer 4 DDoS attacks. Customer Premise Equipment (CPE) mitigation devices prevent the more complex Layer 7 attack vectors.
(See a recommended DDoS Mitigation posture depicted in Figure 2 below).
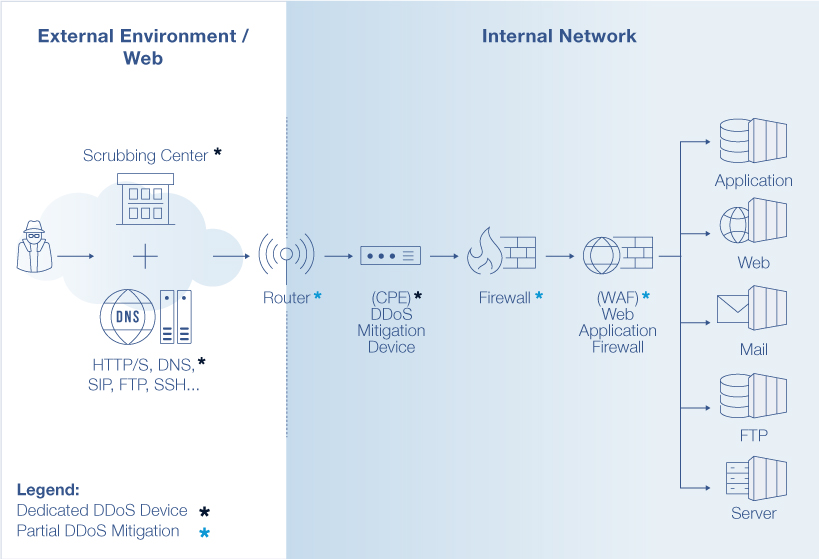
Figure 2
Hybrid mitigation solutions can achieve optimal performance only when the different components (as illustrated in Figure 2 above) are fine-tuned and accurately synchronized with the production network. These mitigation solutions perform only after a DDoS attack is detected. Identifying DDoS vulnerabilities before they become attacks is another challenge altogether.
Companies invest heavily in deploying mitigation solutions; however, security teams cannot test if their mitigation solution is working under different attack scenarios or not without having their service disrupted. Current DDoS vulnerability detection tools require maintenance windows which require downtime.
How to Eliminate the DDoS Vulnerability Gap
In most DDoS attack scenarios, open channels are not detected real-time, and vulnerabilities remain unblocked. That means that DDoS attacks bypass the most robust mitigation solutions.
Since businesses are transforming rapidly, the DDoS vulnerability gap will continue to expand on vulnerable networks. However, it is critical for organizations to detect and remediate the vulnerability gap before attackers can exploit it.
A new patented technology is now available to eliminate the DDoS vulnerability gap and block DDoS attacks entirely.
RADAR™ testing, MazeBolt’s transformative technology, is the only solution on the market today that is always-on, constantly testing, and non-disruptive. It checks every attack vector against all targets to deliver full surface coverage so that your organization is fully protected against DDoS attacks.
With RADAR testing, organizations can eliminate the DDoS vulnerability gap.







