“There are two kinds of big companies in the United States. There are those who’ve been hacked…and those who don’t know they’ve been hacked.”
James Comey, FBI Director, October, 2014
Introduction
Cybercrime in 2014 exceeded even the most pessimistic expectations and far surpassed in magnitude and severity anything seen in recent years.
Looking back at the year we can generally categorize the cyber threats and attacks into the following three main categories:
- New vulnerabilities discovered
- DDoS Attacks
- Phishing and Malware attacks
This blog reviews each of these categories with the aim of acquainting the reader with the main developments of 2014, We’ll also look at how each category of threat played out in the attacks during the year and finally end with a few tips to help strengthen your cyber security posture against attacks during 2015.
1) – New Vulnerabilities Discovered – Heartbleed & Shellshock
When it rains, it pours!
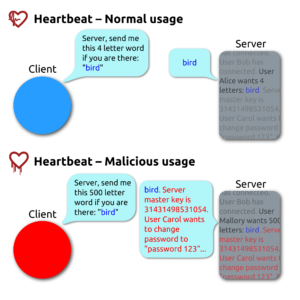
Heartbleed – In April the discovery of Heartbleed shocked the world by disclosing weaknesses in the ubiquitous
“OpenSSL cryptography” library which had been lying there since December 2011. Found in Apache and ngix the weakness is found at the heart of encryption utilized in the SSL is relied upon for privacy in most online operations today, for example:
- Storing credit card information
- User credentials
- Email viewing
- Messaging/Chat services
*Together these servers comprise over 50% of the internet.
To make things worse, quoting heartbleed.com: “Leaked secret keys allow the attacker to decrypt any past and future traffic to the protected services … . Any protection given by the encryption … can be bypassed. Recovery from this leak requires patching the vulnerability, revocation of the compromised keys and reissuing and redistributing new keys. Even doing all this will still leave any traffic intercepted by the attacker in the past still vulnerable to decryption.”
While mitigation efforts around the world were swift (the number of exposed servers one month after the discovery of Heartbeat were estimated at 5%), the sheer scope of exposed servers means that enormous amounts of information were accessed by the wrong people. How they use that information is something that will unfold during 2015.
For a detailed overview of Heartbleed see Troy Hunt’s informative Post.
HeartBleed Damage SummaryEstimated damage due to exploitation of Heartbleed is (as of August, 2014):
|
Shellshock – As if Heartbleed wasn’t enough, in September another set of vulnerabilities (named Shellshock or Bashdoor) were identified that date
back to September 1989 – that’s right Shellshock’ has been there for 24 years! Shellshock allows remote attackers to execute code on the same type of servers that Heartbleed was detected on, which amounts today to over 500 million servers. Quoting Troy Hunt: “The potential is enormous – “getting shell” on a box has always been a major win for an attacker because of the control it offers them over the target environment. Access to internal data, reconfiguration of environments, publication of their own malicious code etc. It’s almost limitless and it’s also readily automatable.”
And like with Heartbleed, the bad news doesn’t end here. The scale of the exposure is compounded by the fact that Shellshock is basically easy to execute and most significantly, there is no authentication required when exploiting it.
Quoting Troy Hunt again: “In all likelihood, we haven’t even begun the fathom the breadth of this vulnerability”
These two bugs are especially noteworthy for the reasons detailed above. They are only the beginning of a very long list of vulnerabilities found during 2014.
2) – DDoS Attacks… gone through the roof!
DDoS attacks essentially represent simultaneous manipulation of many computers / servers (a.k.a “bots”) that are compromised by exploiting vulnerabilities to attack designated targets – the more bots – the merrier!
The scale of public vulnerabilities disclosed this year will make it easier than ever for hackers to harvest bots and exploit them at their will.
It comes as no surprise then that DDoS attacks during 2014 grew in comparison to 2013 in both average attack bandwidth and volume. Over 100 attacks were spotted larger than 100GB/sec in the first half of 2014 with the largest at 321 Gbps.
Quoting John Summers, VP, Security Business Unit at Akamai Technologies: “DDoS attack size and volume have gone through the roof this year. … ”
Banking industry – 2014 saw noteworthy guidance issued basically acknowledging the role DDoS is playing in disrupting regular bank operations, damaging reputation and straightforward fraud.
Financial institutions are expected to – “address DDoS readiness as part of their ongoing business continuity and disaster recovery plans and to take certain specific steps, as appropriate, to detect and mitigate such attacks.”
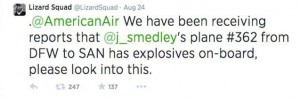
And last but definitely not least is Sony, who have been the focus of a number of crippling cyber-attacks this year. Starting in August when a DDoS attack impacted online services for both Sony’s PlayStation Network and the Sony Entertainment Network. While Sony’s representatives said that the company has “seen no evidence of any intrusion to the network and no evidence of any unauthorized access to users’ personal information” a flight with the president of Sony Online Entertainment, John Smedley was redirected after the following tweet appeared.
DDoS Damage SummaryAn Incapsula study for 2014 covering 270 North American Companies found that 40% of respondents had been hit by a DDoS attacks during 2014.
|
3) – Phishing and Malware
Phishing is the attempt to acquire sensitive information such as usernames, passwords, and credit card details… by masquerading as a trustworthy entity in an electronic communication. Malware, short for Malicious Software, is any software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. Malware is often disguised as benign software in phishing communication or web pages for users to download and install.
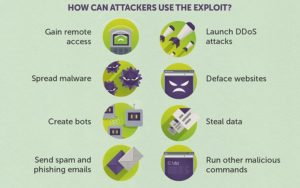
One of the new cyber-attack methods identified during 2014 was executed using Phishing and Malware to “…gain access to confidential information. With this information, hacktivists successfully compromised third-party content feeds on popular media websites, such as CNN, the Associated Press and others.”
The image to the right >> is an illustration of such third party content that could be manipulated to lure readers into click on the content which would load web pages designed to steal sensitive information or install malicious software on their computer.
While DDoS attacks are meant to “Knock- out” a company’s services or be used as a smokescreen, hackers use Phishing to collect sensitive data that can be used for fraud, criminal activity or for harvesting future cyber-attacks.
Because Phishing and Malware are disguised they are mostly discovered only after the damage is done and this brings us back to the second cyber-attack Sony experienced in December this year.
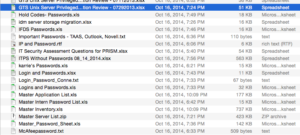
The December attack on Sony was probably the biggest ever seen in terms of confidential information made publicly exposed. Surprisingly however, experts are saying it was not necessarily that difficult to penetrate Sony and access information. Passwords were saved precariously on Excel files with self-revealing file names exposed and unencrypted as the image to the right from Gawker illustrates.
Cost of Phishing & Malware 2014 – SummaryOf total cost of cybercrime, damages caused to U.S. companies approximately 13%, are estimated to be associated to phishing and social engineering.
|
Conclusions
Well, that’s the bad news ….. but there is also some good news.
If there’s one thing we can learn from attacks seen during the year is that by observing simple security rules and practices in a disciplined way we can make it difficult for cyber criminals to do damage.
Three simple rule are:
- Passwords: Secure your information (Never save passwords in un-encrypted files – especially ones that contain passwords for access to most of the IT infrastructure!)
- Emails and Awareness: When there is doubt, there’s no doubt. Educate your employees on Phishing and how to identify it, test them regularly with Phishing simulations. Most data leaks in 2014 began with a successful phishing attack.
- Trust but Verify: Make sure your IT team is up to speed on the latest weaknesses in your IT infrastructure, do this through regular and realistic threat assessments. Make sure all you systems react as expected to automated bots and persistent attacks. This is likely the most important ongoing aspect to your cyber security posture having any real reliability!
About MazeBolt TechnologiesMazeBolt Technologies is a Cyber Security Threat Assessment Company that has developed an unparalleled Threat Assessment Platform (TAP) which covers: (i) DDoS, (ii) Phishing & (iii) Vulnerability scanning in a unique, unified and user-friendly interface that provides organizations with: Actionable insights into their DDoS protection, external vulnerability insight, concrete solutions to vulnerabilities discovered and sophisticated phishing simulations and training courses to create awareness internally. |