Blog
The Real Reason DDoS Succeeds – And What Your DDoS Protection Is Missing
Most DDoS protections miss the real threat: misconfigurations. Learn how to close critical gaps and prevent damaging downtime with real-world insights.

Leveraging AI to Protect the Largest Attack Surfaces from DDoS: Introducing RADAR SmartCycle™
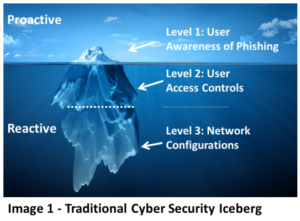
How DDoS Attacks Unfold: Reactive vs. Proactive Approaches to Defense

Crippling DDoS Attacks Strike Europe – Webinar Recap

The Impact of AI on DDoS Attacks – Are Attackers Gaining the Upper Hand?

F5 Joins MazeBolt’s Preferred Remediation Program

SSL Decryption is DDoS-Vulnerable

Cloudscraper: The Most Vulnerable HTTPS Vector

Geo-Blocking: a Band-Aid

Hacking Anonymous Sudan: Behind the DDoS Mask

DDoS Protection is Plagued with Vulnerabilities

Money’s in the Bank – DDoS Attackers Know That