Blog

Is Your Network Configured to Prevent Damaging Downtime?
Learn how improper network configurations leave organizations vulnerable to DDoS attacks. Explore best practices to prevent downtime in MazeBolt’s latest eBook
Note to Banks: Proactively validate your DDoS mitigation
MazeBolt CEO Matthew Andriani @ Channel i24 on OpIsrael

2015 in DDoS Attacks – Highlights of noteworthy DDoS attacks in 2015

Trust your DDoS mitigation configuration. No, really.
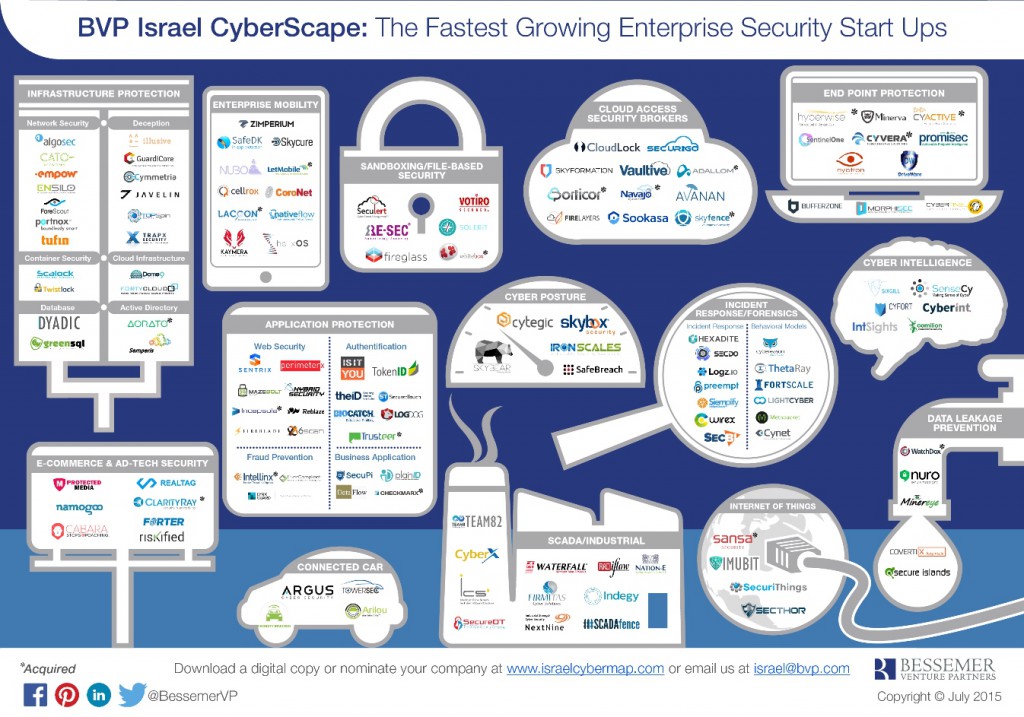
BVP lists MazeBolt as one of the fastest growing Enterprise Security Startups

DDoS Extortion – Biting the DDoS Bullet
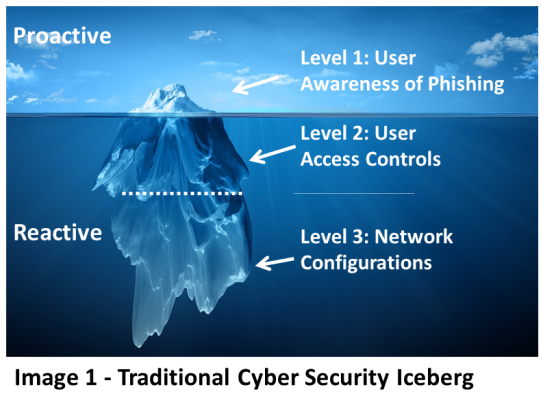
The Cyber Security Iceberg – Which Way Is Up?

















