Blog

Cost of Damaging DDoS Attacks in 2025: Annual Trends Report
DDoS attacks surged 30% in 2024. Learn key trends, vulnerabilities & how to strengthen defenses in MazeBolt's 2025 DDoS Trends Report.

Learning from Air Crash Survivors: A Lesson for Life

MazeBolt’s Security Blog is Now Among Top 100 Cyber Security Blogs

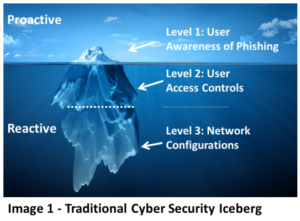
Importance of Proactive Feedback for DDoS Mitigation

DDoS Defenses – Newsletter February 2020

7 Reasons to Understand Your DDoS Kill Chain

Under DDoS Attack? Initiate these 5 Steps Immediately

Five reasons why your DDoS Mitigation might fail