The new approach to DDoS Security:
Preventative. Proactive. Automated Protection.
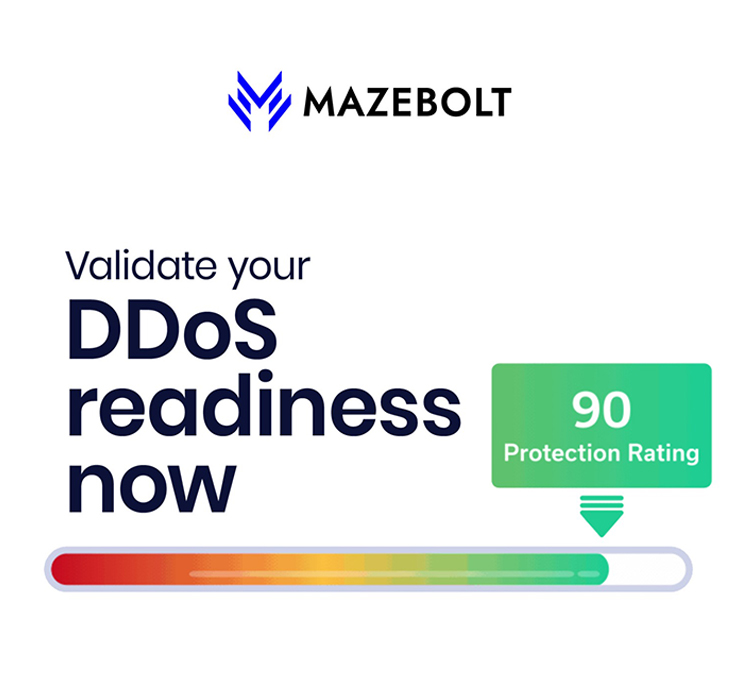
MazeBolt presents the only reliable way to avoid a damaging DDoS attack: Identify and remediate all DDoS vulnerabilities with the world’s first non-disruptive DDoS testing solution.
simulations annually
each target
in DDoS readiness
coverage
A paradigm shift in DDoS security - with zero downtime.
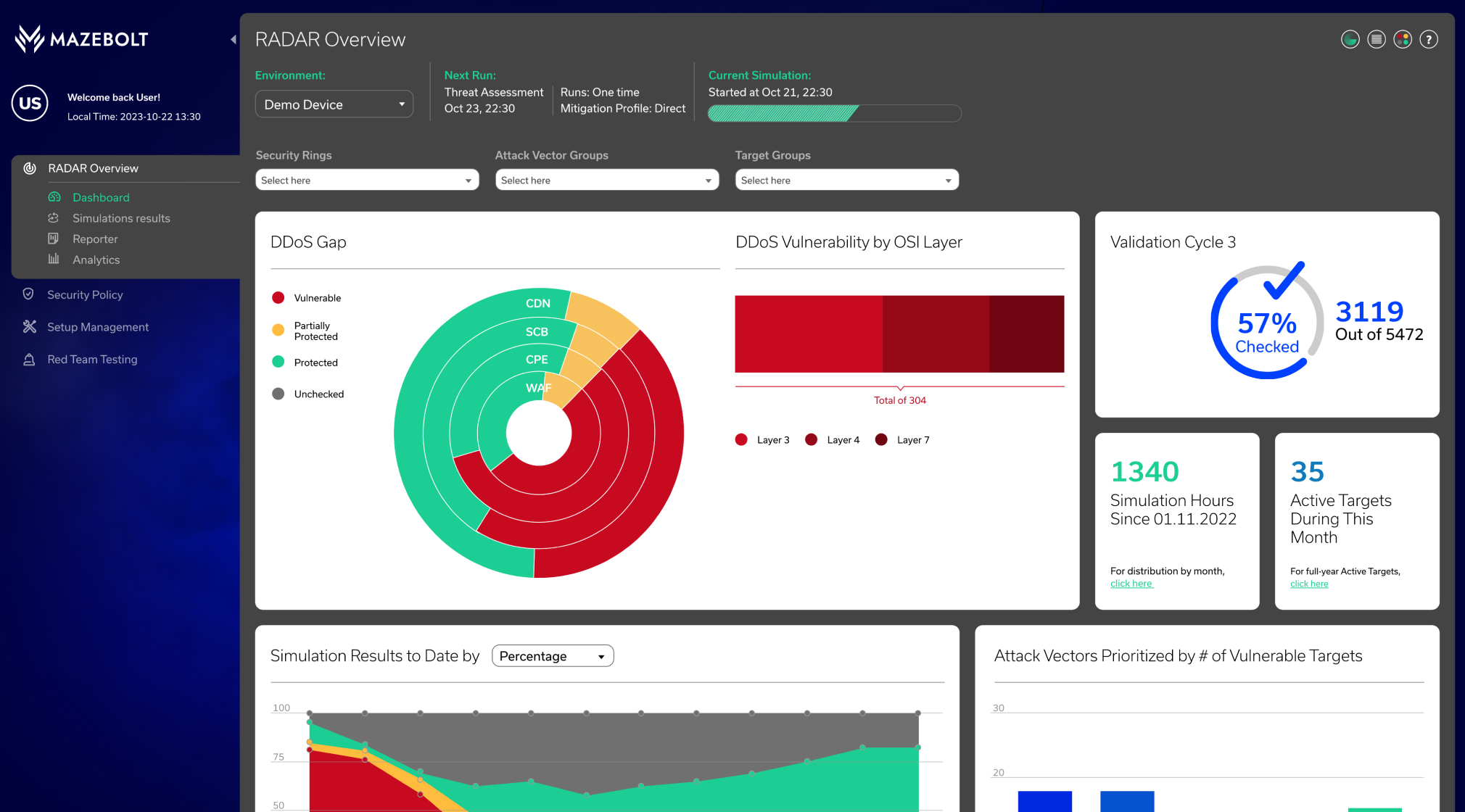
MazeBolt RADAR™ identifies and enables the elimination of DDoS vulnerabilities on every layer of DDoS protection, empowering stakeholders to adopt the transformative approach of automated DDoS protection. The solution provides enterprises full visibility into their online services, testing tens of thousands of DDoS attacks without interrupting business operations.
The only way to avoid damaging DDoS attacks is to have zero vulnerabilities.

Continuously test all layers of your DDoS protection

Uncover DDoS protection misconfigurations

Prioritize & remediate vulnerabilities
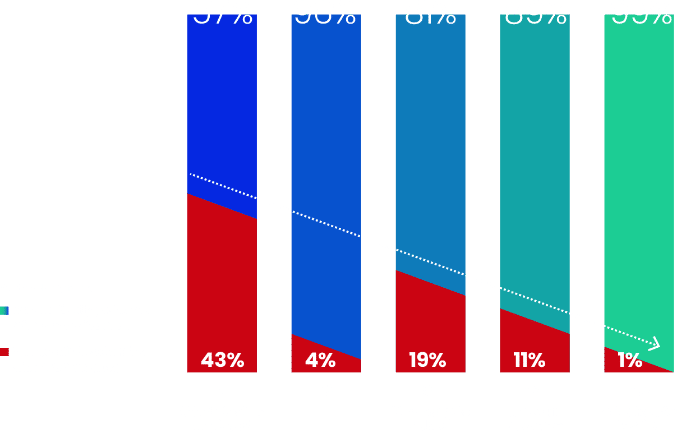
Say goodbye to manual time-to-mitigation and emergency response time SLAs.
Achieve fully automated DDoS protection, with all security layers up-to-date against all known DDoS attack vectors with zero downtime.

Maximize return on your existing DDoS protection investment
Measure your DDoS protection’s effectiveness while gaining cyber-insurance premium reductions. MazeBolt RADAR eliminates the risk of successful DDoS attacks by continuously testing and validating every potential attack vector for vulnerabilities – without interrupting business operations. RADAR is an essential solution for enterprises seeking to level up their current DDoS protection systems for the highest level of security.

Unparalleled Visibility
Gain complete visibility of your online services with continuous RADAR testing.

Identifies and Validates
Test to validate that all your vulnerabilities have been fixed correctly.

Non-disruptive
Continuously test production environments - with zero operational downtime.

DDoS Protection Agnostic
RADAR works with all DDoS protection providers.