What’s a DDoS Mitigation Gap?
A DDoS Mitigation Gap occurs whenever DDoS traffic bypasses a company’s DDoS mitigation defenses to penetrate the target network. DDoS mitigation gaps are a major source of concern for companies, since there is very limited visibility of DDoS mitigation gaps without in-depth analysis and testing.
Why do DDoS Mitigation Gaps happen?
In an ideal world, once a DDoS mitigation posture has been deployed and configured satisfactorily all DDoS traffic would be mitigated, there would be no leakage and no DDoS Mitigation gaps.
However in reality this is seldom the case.
To understand why we need to understand the complexity that DDoS attack vectors pose for mitigation devices & services.
DDoS Attack Vectors Complexity
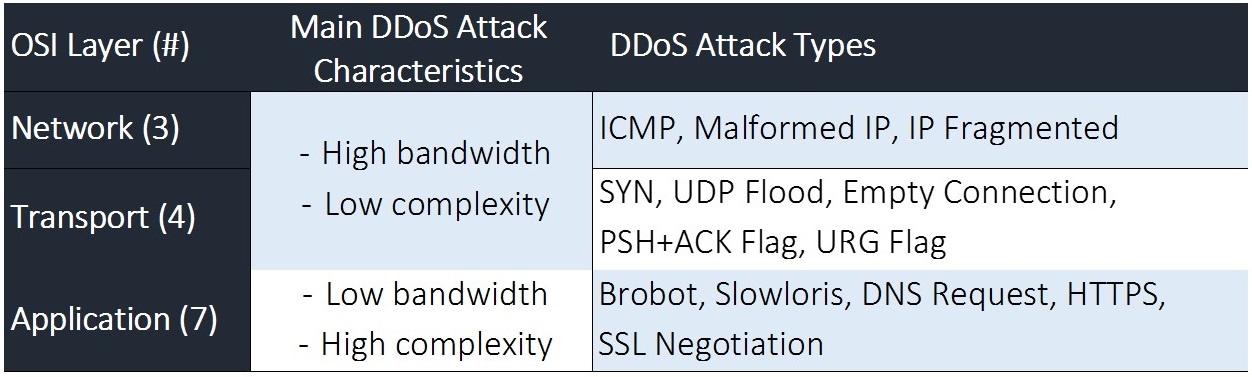
First, DDoS attack vectors strike networks on three different Open Systems Interconnection (OSI) layers. Second, attacks from the different OSI layers generally have different characteristics and third, within each of these three OSI layers DDoS attack vectors take many different forms, thereby significantly complicating attack identification and mitigation (See Figure 1 for OSI Attack characteristics and attack type examples).
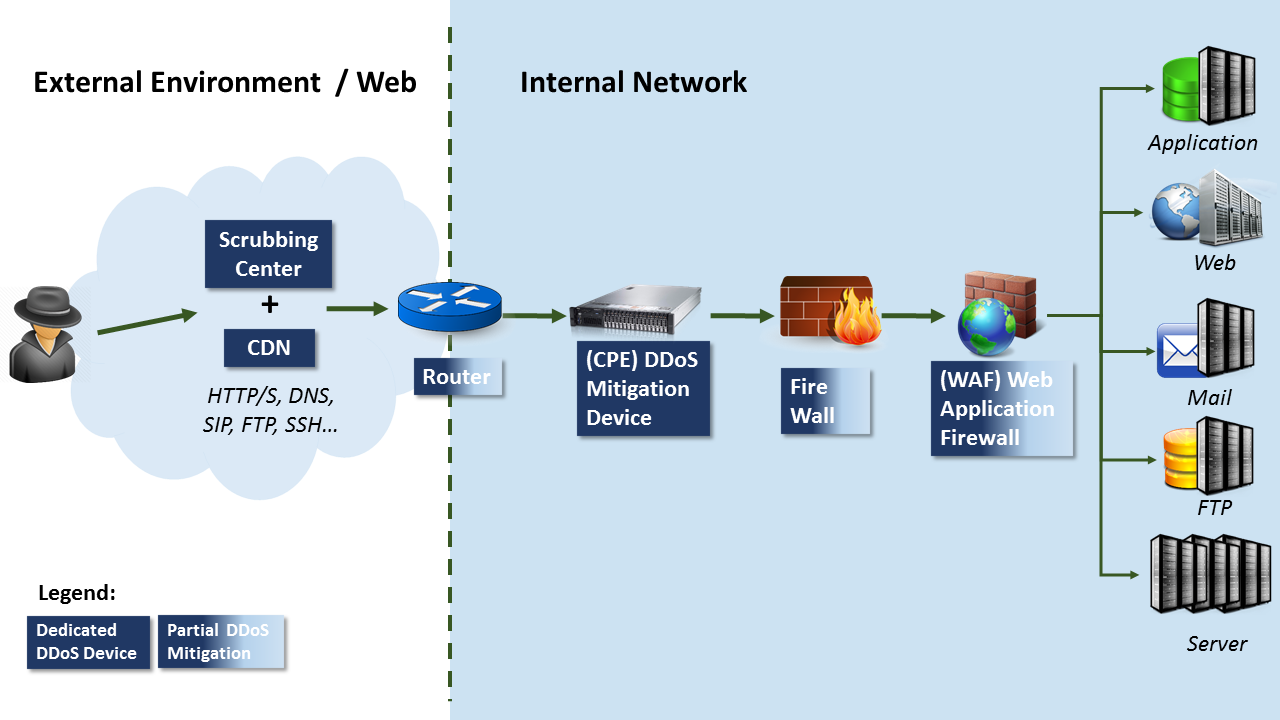
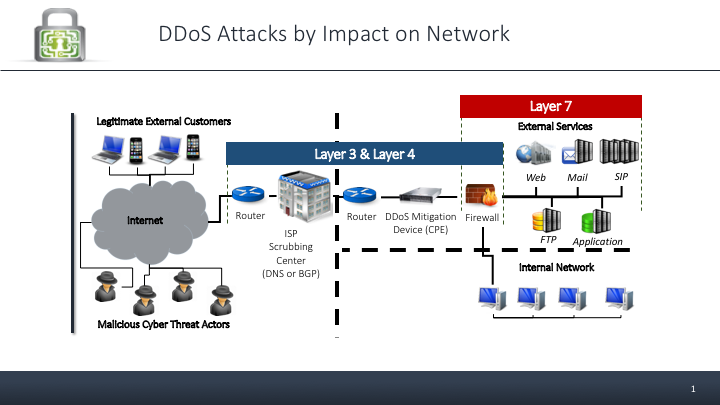 Figure 2 – Impact of DDoS attack vectors on a typical network
Figure 2 – Impact of DDoS attack vectors on a typical networkDDoS Mitigation – No Silver Bullet
Due to this complexity, mitigating DDoS attack vectors has no single “Silver Bullet” but rather a combination of DDoS mitigation systems. These systems include Cloud based Scrubbing centers and Content Distribution Networks (CDN) that are usually employed to mitigate high bandwidth Layer 3 & Layer 4 DDoS attacks as well as Customer Premise Equipment (CPE) mitigation devices that are mostly used to fend off the more complex Layer 7 attack vectors (See a recommended DDoS Mitigation posture depicted in Figure 3 below).
Whether companies use one or more mitigation systems to protect their networks and online services from DDoS attack vectors, there are many different components (as illustrated in Figure 2 above) that need to be finely configured and accurately synchronized with the production network it is defending for optimal mitigation performance.
Going back to our ideal world, let’s assume for a moment that we’ve chosen the optimal DDoS mitigation posture and our vendor has fine-tuned all components so both network and mitigation are perfectly synchronized
At this point in time – our mitigation is perfect, we have no DDoS mitigation gaps.
Networks Constantly Changing
The competitive landscape, however, constantly pushes companies to improve their service offerings to drive revenue and make internal operations more efficient to cut costs. Companies’ networks constantly need to adapt to new servers and services that are being added to networks.
In order to synchronize DDoS mitigation perfectly with the changing network we would need to match each network change with a respective fine-tuning in the DDoS mitigation posture.
In reality, companies do not constantly re-configure and fine-tune their DDoS mitigation postures and this is precisely where DDoS Mitigation Gaps emerge.
Visibility on DDoS Mitigation Gaps?
The problem is that visibility of DDoS mitigation gaps is nonexistent to cyber security personnel responsible for production uptime. Companies do not know how well their mitigation is performing or where their configuration problems are, leaving them and their vendors to troubleshoot issues at the very worst possible time, that is, when systems are brought down by a DDoS attack vector.
Proactively Identifying DDoS Mitigation Gaps
The most effective way to identify DDoS Mitigation Gaps proactively is DDoS Testing. DDoS Testing is an iterative process of simulating a wide variety of real DDoS attack vectors in a highly controlled manner to allow companies to understand where their mitigation is performing and more importantly, where it isn’t.
Insight from an effective DDoS Testing Program will highlight four key factors:
- Purely technical configuration issues with DDoS mitigation devices & services
- Vendor performance and SLA issues (When under attack is your vendor there? How quickly do they have respond and the up-time to bring system back to normal ?)
- Response processes & procedures (Are roles and responsibilities clear? When under DDoS attack do your team members each know what to do and how to do it?)
- Communication channels (Does your team know where to get a packet capture from and who to send it to?)
And thereby enable companies to work at consistently reducing their DDoS Mitigation Gaps to a minimum.