Spear-phishing seems to be everywhere these days.
According to Symantec’s recently published 2014 Annual Report, five out of every six large companies (2,500+ employees) were targeted with spear-phishing attacks in 2014, a staggering 40 percent increase over the previous year.
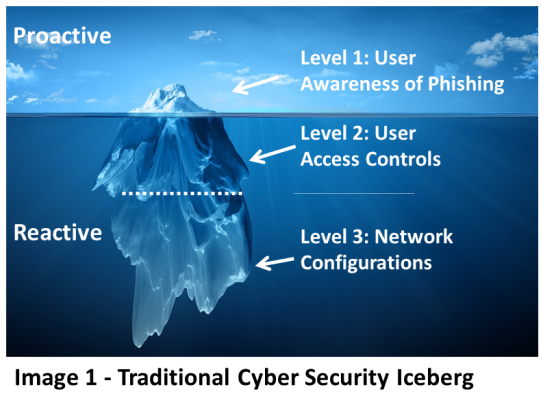
The Cyber-Security Iceberg
When discussing the importance of strengthening user awareness of phishing with our customers, one of the main points of feedback we hear is that while awareness of phishing is clearly important in ensuring a secure network, at the end of the day, it is such a ‘fluffy’, difficult-to-effectively-manage factor, that only represents the [visible] tip of the iceberg when compared to the wealth and number of automated analytical tools and defensive devices companies have at their disposal. (See Image 1)
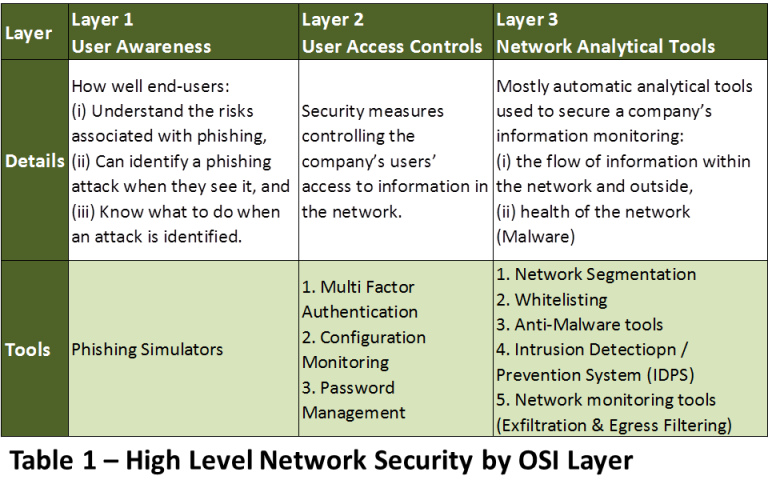
The main effort in fighting cyber-attacks and valuable data loss they argue is not by focusing on the iceberg’s ‘awareness’ tip but rather on its submerged ice mass. Namely, the many analytical and mostly automated tools and processes companies have for securing their data (See detailed in Table 1).
Moreover, it is not uncommon to hear industry experts claim that because user awareness is traditionally such a difficult factor to manage, companies should work under the assumption that they’ve already been compromised by cyber-criminals and use the sophisticated analytical tools available to protect their networks instead.
The Best Defense is Offense
Security is most effective when practiced proactively, not re-actively. Take public transport security for example.
Airports and airlines invest massively in preventing terrorists from boarding airplanes, not because they don’t have measures on board to mitigate damage, they do. But once an armed assailant has boarded a plane the question becomes not whether damage can be avoided but rather how much of it will be caused.
The fact that the traditional concept of PROACTIVE campaigns to strengthen user awareness is largely ineffective and more challenging to address and manage, on the one hand, and the REACTIVE analytical and automated security measures, on the other, are easier to manage and execute – should not be confused with their impact on securing your network environment.
Would you accept reactive security measures on your next flight? So why accept them with your business’ Intellectual Property? Or your bank account details?
Looking at the Traditional Cyber-Security Iceberg above, we argue that this view is driven more by the degree of control people believe they have over the different security layers than of the actual security each layer commands.
Inverting the Cyber-Security Iceberg – Take Control
To start with, phishing awareness tools, such as Phishing Simulators should not require any security softening such as white-listing of source domains or IPs. The best Phishing Simulators in the market have been tested to work in real life conditions.
Second, even if an organization decides to white-list a Phishing Simulation tool (not all admins using the software may understand the various rules when it comes to constructing phishing simulations that avoid spam filters) the fact employees are continuously being tested and trained when they fail will undoubtedly raise the awareness bar significantly and prevent code being executed or credentials stolen.
Third, today’s phishing simulators translate that ‘fluffy’, difficult-to-effectively-manage awareness of phishing into detailed quantifiable metrics that executives can manage with.
Are your IT managers measured against Phishing Awareness KPIs?
They should be.
Lastly, phishing simulation tools should be able to identify client side vulnerabilities that your employees are running in outdated software, plugins or browser versions.
Understanding which users are most susceptible to phishing attacks and detection of client-side vulnerabilities empower managers to focus resources effectively with Layer 2 & 3 Configurations.
Building your cyber security strategy on the basis of the inverted Modern Cyber Security Iceberg stands you the best chances of proactively meeting today’s cyber security threats.