We started this series with an introduction to how criminals have adapted their cyberattacks around the abundance of personal information available online, and continued with two posts highlighting key phishing identifiers: Email Addresses and Links. This post opens with a few more phishing related tips and wraps the series up with concrete steps you can take to limit your Social Media exposure online.
Your intuition, Trust it.
No matter how well cybercriminals profile you they will never really know who they are actually phishing and therefore there will always be something out of context about their communication.
Four phishing pitfalls that should trigger an alert and your intuitive feeling of ‘phishing discomfort’ are:
1. Attachments: There is no foolproof way to identify a malicious attachment – therefore the rule is NEVER to open an attachment before you have verified with the sender that they actually sent the file. (Cybercriminals may have compromised the sender’s email account).
2. Greetings: In most cases cybercriminals will not know your name and will therefore start their communication with a generic “Hi”, “Good day”, “Dear Customer” etc.. . While this could pass for a friend or an acquaintance, that is not the case for your Service providers and online accounts who know your name and should use it when they communicate with you.
3. Spelling Mistakes / Signatures: With most people nowadays sending emails on the fly from their portable devices, spelling mistakes and generic email signatures are not uncommon. However, official communications from Service Providers should not have either.
As a principle, when in doubt, there is no doubt!
Whenever there’s something phishy about an email – ALWAYS check the two key phishing identifiers (Email Addresses and Links) and guidelines above to make sure.
Unshare Yourself
Social media has transformed our ability to share our lives and connect with friends, family members and acquaintances from around the world, updating them in near real-time with
There’s a sharp contrast though, between the ease with which we are able to share every part of our lives, on the one hand, and the degree of control we have over those records once we’ve uploaded them into cyberspace, on the other.
There are two main aspects controlling how slippery the ‘Sharing Slope’ is:
(i) What we share in the first place, and
(ii) Who we share it with.
What we each choose to share online is a personal question
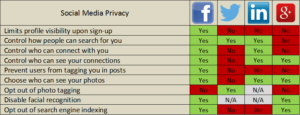
Social Media Privacy Settings (
Click for better view) Source: Kristin Burnham, ‘How the top social networks compare on privacy — in one handy chart’
that largely depends on who we believe we’re sharing it with. It’s important to understand that the answer to: “Who can see what I’m posting (by default)?” differs largely from
On Facebook, for example the default privacy setting on all shared content was Public until only last year. On Google+, LinkedIn and Twitter the default setting is still public. (See Image 1 for more details)
We all know that an enemy’s enemy is a friend, but is a friend’s friend also a friend?
What happens when a friend ‘likes’ a photo you’ve posted? Do their friends see it as well? Would you have posted it if you knew they would?
All this sharing gets somewhat complicated and rightfully so – it is! We recommend focusing initially on the two aspects above (i) What we share in the first place, and (ii) Who we share it with. Answering these two questions should go a long way in leveling your Social Media ‘Sharing Slope’ and giving you more control over the material you share online. Kristin Burnhams’ article referenced above is a great place to start clarifying your Social Media privacy status one step at a time.
We hope this series has helped clarify some of the complexity around today’s phishing-related cyber threats and moreover provided you with tangible steps you can start taking to limit your exposure.
Stay tuned!