When was the last time you checked to see if your security defenses were prepared for a major attack? Organizations occasionally contract for penetration testing, red team v. blue team, and phishing training. Generally, DDoS testing is not on that list.
While less frequent than many other types of attacks, DDoS attacks can potentially be the costliest in terms of mitigation, operating losses, customer retention (or lack of), reputation, legal liability, staff time, and regulatory noncompliance.
Third-party Protection: Many enterprises depend on third parties for DDoS protection as part of a suite of general service offerings. But those protections may not be good enough. These Internet service providers (ISPs), MSSPs, and other scrubbing centers are not the ones who face the biggest losses when your company is the victim of a major ISP DDoS attack. They DO provide some protection, but that may not be enough for the type, volume, and intensity of the attacks that you may face. Remember, your potential losses can be several times larger than your ISP’s.
Some companies may choose to supplement the DDoS protection they get from third parties with another layer of protection. Even this extra protection may not be enough.
The only way to ensure that a DDoS infrastructure is ready for the hundreds of variants of DDoS attacks is to test it.
Comprehensive DDoS Testing: DDoS testing involves a comprehensive battery of specially tailored “attacks” to force the system to defend itself. As these are coming from a white-hat hacker infrastructure, the tests won’t cause any permanent damage – unless the system is already so badly broken that the initial tests reveal significant flaws.
DDoS testing is a systematic process, to validate all mitigation mechanisms are working together as expected and automatically, against the most common attack vectors.
Determine the Testing Baseline
- MazeBolt’s Baseline Testing Process has been fine-tuned over the years to ensure that the system is put through a comprehensive battery of tests, based on the latest attack technologies and strategies used by cybercriminals.
- MazeBolt’s Baseline testing methodology provides a standard KPI easily understood by, technical personnel, executive management and the mitigation vendors, allowing for quick resolution of issues identified.
The organization will receive a clear report that describes the effects the tests have had on the system. The report
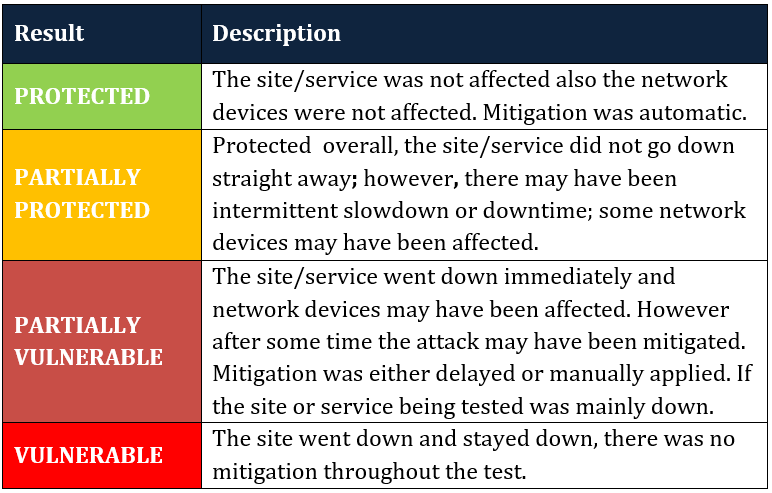
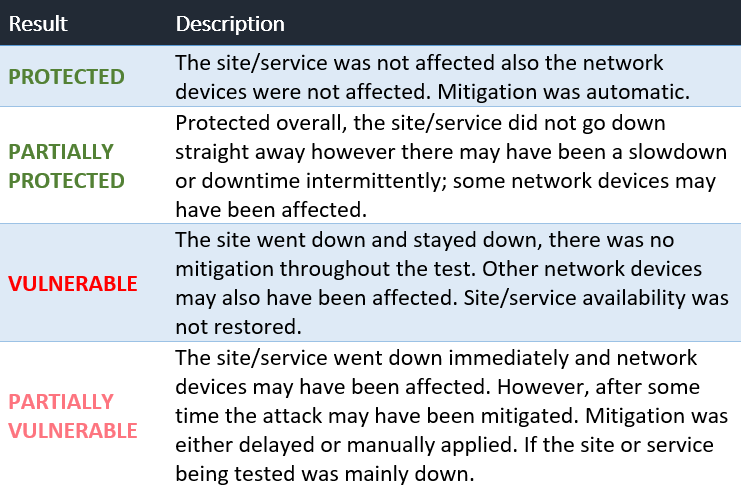
- Provides KPIs of the results of each type of test with Protected, Partially Protected, Vulnerable, and Partially Vulnerable.
- Breaks down the results further by explaining exactly what the four categories mean within the test.
- Provides comments for each test completed during the Baseline testing
Sample Testing Results
- Partially Protected: Empty Connection Flood – Layer 4 – FW went to 1.1 million CPS. MazeBolt couldn’t connect. Eight alerts on FW load during that period
- Vulnerable: PSH + ACK Flood – Layer 4 – The site went down completely, and FW went to 100% and stayed there; traffic was not being mitigated. 219 Mbps leakage recorded, likely increasing
- Partially Vulnerable: SSL Renegotiation Attack – HTTPS site was unreachable during the attack. HTTP wasn’t reachable and then was reachable for others. Because the daemon went down, the scrubbing provider detected a DDoS SYN Flood attack, which possibly allowed the site to recover.
Recommendations: After the first set of tests is performed, the Protected-Vulnerable report is followed by specific recommendations to address the flaws with the customer’s mitigation vendor/s. The recommendations could range from specialized instructions to the IT mitigation team to a comprehensive report the organization delivers to its hosting provider or DDoS technology solution provider that details the customization required to fully protect the individual organization’s infrastructure.
Did the Configuration Improvements Work?
Once you’ve fixed the flaws, the next step is to check that the mitigation steps were properly applied. MazeBolt will test the system again in a Baseline Validation test, focusing on the areas that were partially protected, partially vulnerable, and vulnerable previously. The attacks will once again verify those areas of DDoS mitigation.
Download the guide below to increase the effectiveness of your DDoS mitigation solution.