There has been a significant increase (more than a double) the number of attacks of 5Gbps or under. These smaller and more carefully targeted attacks can aim to disable specific parts of a company’s infrastructure and can easily bypass the victim’s attention. (“Per Neustar Study”)
DDoS Attacks Have Evolved
The aim of DDoS attacks, is still to bring a business down, but the tactics have changed. These smaller, smarter, sneakier attacks are difficult to detect and block by current DDoS Mitigation technology. These sneaky and tiny attacks go “below the Radar” of a set thresholds, look like a steady slow down in service delivery and may mislead business to look for a solution on other fronts.
Businesses have advanced
We are in a new era of technology where organizations are disrupting industries with Digitization and cutting edge technology.
All businesses, regardless of size have implemented a multitude of digital systems to sell to and service their customers, not just locally or in a few territories, but globally and 24 x 7. Businesses have had to make these adjustment to compete whether they like it or not.
Having said the above, Digital services are exposed to new threats from providers connected to their services, to different territories hackers and so on.
Then Why Your DDoS Mitigation is STILL the SAME?
The types and complexity of attacks have developed along with Digital Transformation. However, we are still using DDoS mitigation technologies, as we know them, for years. We call these technologies Legacy DDoS mitigation, for good reason.
This new reality of a rapidly changing digital world demands that we rethink how we detect and mitigate smart and sneakier DDoS attacks. Vulnerabilities are constantly being opened up by network configuration changes, IT services additions and other changes to the IT environment. In this fast-paced digital world DDoS defenses must quickly catch up with the changing Vulnerabilities.
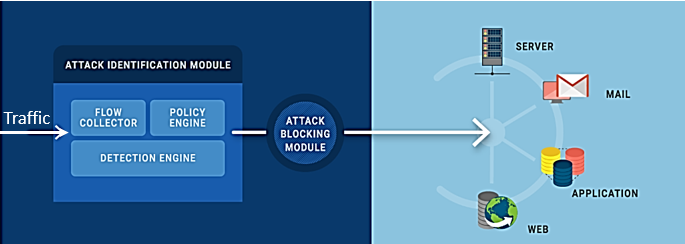
- DDoS Mitigation Technology Today: DDoS Mitigation is designed to analyze traffic coming from different sources. Its AI-based technology too focuses completely on traffic behavior, analyzing anomalies and understanding
past trends to decide whether the traffic is legitimate. This entire mechanism is one way, because of the assumption that DDoS Mitigation once configured protects entire infrastructure irrespective of changes in the network.
- Challenges to DDoS Mitigation: On the other hand, in the world of Digital Transformation the organization’s infrastructure and its related network change continuously. For example, third party Vendor has given access to enterprise server or simply added new mail server into the network, new camera configured for global security etc. No DDoS Mitigation is designed today to automatically adapt to such changes taken place in the network, where a manual process fails to address the challenge, leaving networks vulnerable and exposed to DDoS Threats, right after few days from the system configuration.
How Shall We Close this GAP?
DDoS Mitigation today needs a Proactive Feedback Mechanism
You have the best in class DDoS Mitigation that has AI technology to analyze and eliminate bad traffic, specifically designed for the network it was initially deployed to. But what your DDoS Mitigation also needs is a PROACTIVE FEEDBACK MECHANISM to identify vulnerabilities developed in the network due to changes.
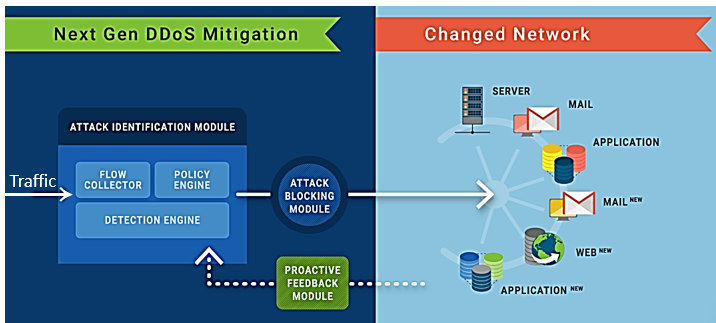
MazeBolt’s patented technology i.e. Proactive Feedback Module does exactly this. Proactive Feedback Module brings complete visibility into web-facing networks without disrupting the IT operations. It then speaks to DDoS Mitigation Vendor to fix postures for the vulnerabilities generated due to network changes. And validate again to ensure that DDoS Mitigation works well on the changed network, this is an ongoing 24 x 7 process. To understand more about this ground-breaking technology, visit the webpage.

 past trends to decide whether the traffic is legitimate. This entire mechanism is one way, because of the assumption that DDoS Mitigation once configured protects entire infrastructure irrespective of changes in the network.
past trends to decide whether the traffic is legitimate. This entire mechanism is one way, because of the assumption that DDoS Mitigation once configured protects entire infrastructure irrespective of changes in the network.
