You cannot protect what you cannot see.
There was recent news that Australian banks are being targeted by DDoS extortionists. That hackers are sending emails to banks asking for large payments in Monero and threatening DDoS attacks if their demands aren’t met. In spite of technological innovation, financial institutions, especially banks, are unable to prevent DDoS attacks.
Therefore, unless security teams are aware that DDoS vulnerabilities exist and where they are located, they can’t take corrective measures to eliminate them. The primary issue security teams face today in managing DDoS threats is the lack of visibility on just how secure their DDoS defenses are.
DDoS mitigation technologies don’t know how to auto-tune
Today’s DDoS Mitigation works in the following way:
- First, DDoS mitigation policies are configured (in the ‘Attack identification module’) and deployed in accordance with how the mitigation vendor understands your network layout.
- If under attack, the ‘Attack identification module’ analyses incoming traffic according to its policy configuration. It then filters out attack traffic, which is blocked by the ‘attack blocking module’. The remaining legitimate traffic is then passed onto the requested service, e.g. MAIL, WEB.
- Traffic is only filtered out and blocked, assuming that the underlying network layout has not changed since the initial deployment and mitigation policy setup, as shown in the figure below:
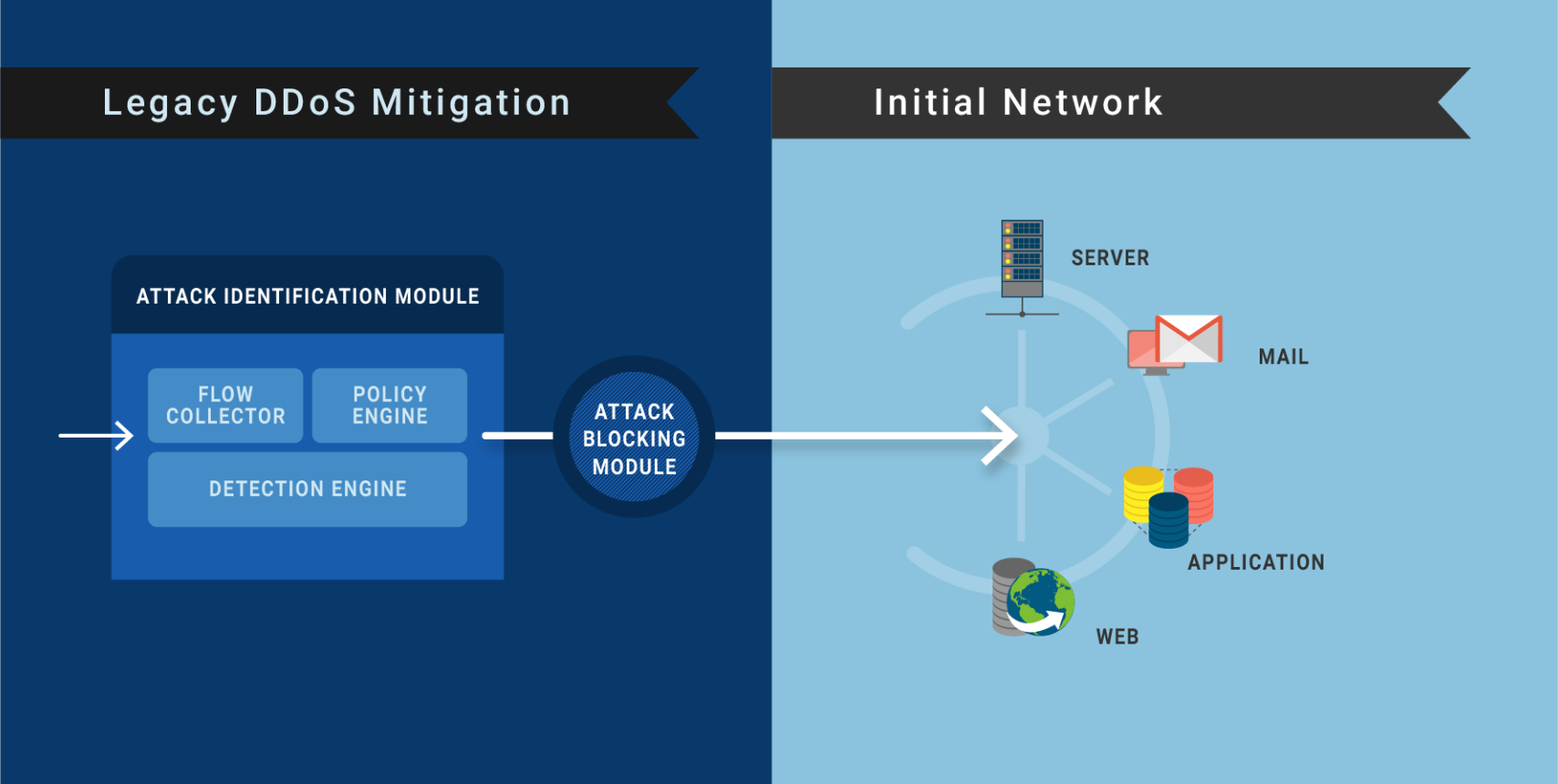
Initial DDoS Mitigation configurations with the underlying network
In reality, however, the underlying network changes continuously.
In some cases, new mail servers are added to the network. Third-party vendors may have been given access to other servers. Regardless of the change, networks and their services change constantly.
With each network or service change, it is necessary that the DDoS mitigation policy is fine-tuned, or else DDoS vulnerabilities are left wide open.
As a matter of fact, this level of diligence in making a change to the DDoS mitigation policy each time a network or service change happens is not viable, nor is it a part of any enterprise’s change request process. Furthermore, there is no feedback loop or two-way communication that is sent to the DDoS Mitigation’s ‘Attack identification module’ to update that any changes have taken place in the underlying network.
Can’t fix what you can’t see or are not aware of!
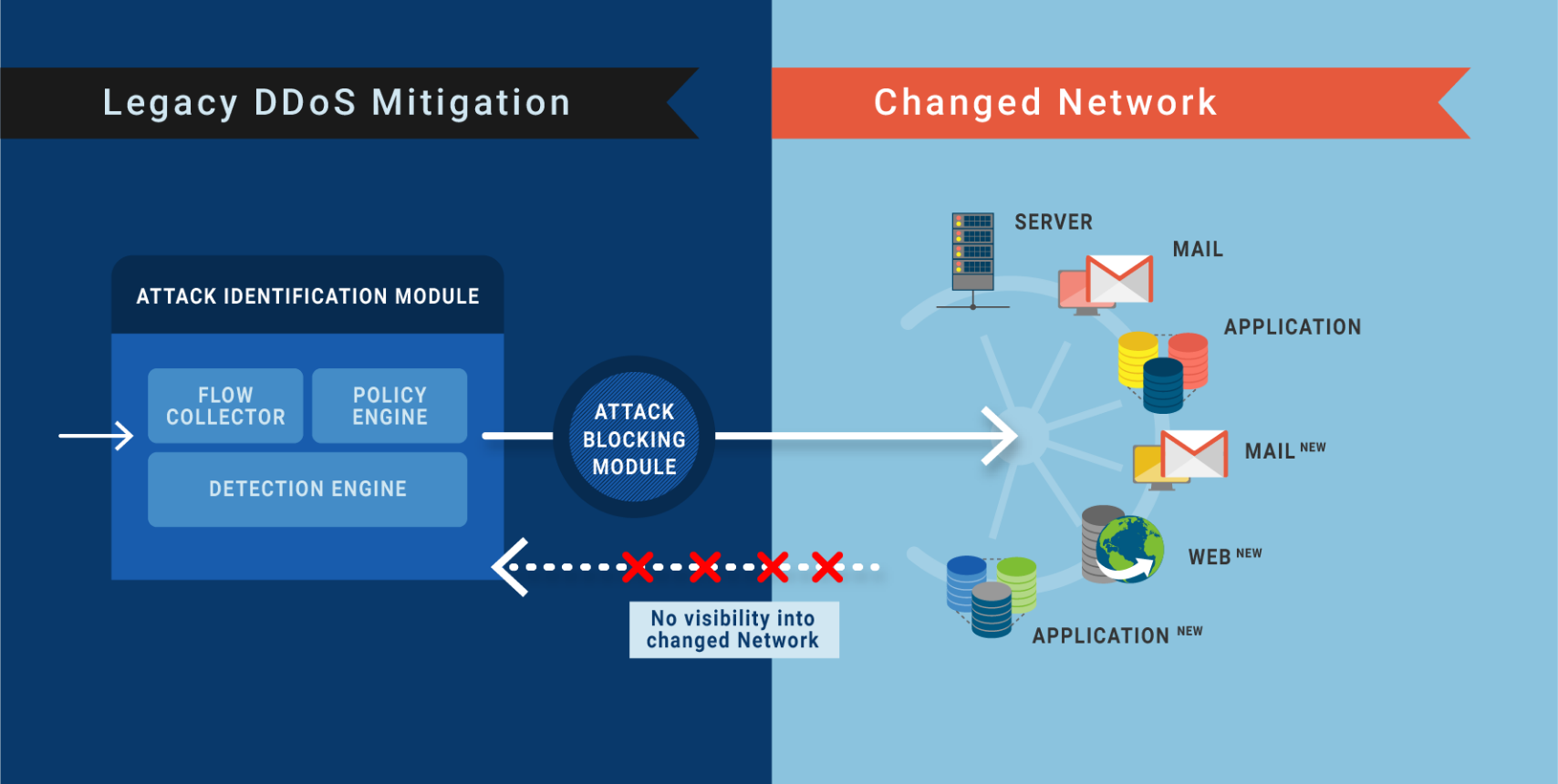
No feedback is given to DDoS Mitigation when the network is changed
As the network changes, it is important that ‘Attack identification module‘ policy configurations are reviewed to ensure that the policies defined are in line with what needs protecting.
When the ‘network’ or ‘service’ changes, CURRENTLY,‘ Attack identification module’ policy updates are NOT automated. DDoS vulnerabilities are opened up, and if the security teams are not able to see where the vulnerabilities lie, they can’t eliminate them. Continuous feedback is an essential requirement to close DDoS Vulnerability Gaps. Existing DDoS vulnerabilities become the target of hackers and are exploited fast. This causes downtime.
As per The State of DDoS Protection, even with current best-in-class DDoS Mitigation in place, 65% of companies will encounter some type of downtime within the next 12 months. The average DDoS security gap of enterprises is 48%. RADAR™ brings down the gap to under 2%.
See where the vulnerabilities lie and defend them before getting exploited
RADAR™, MazeBolt’s new patented technology solution, is part of the MazeBolt security platform. RADAR™ simulates DDoS attacks continuously and non-disruptively. Delivering advanced intelligence through straightforward reports on how to remediate the DDoS vulnerabilities found.
Closing the DDoS gap by assisting your mitigation solution to fix ongoing security gaps before they are exploited. Using RADAR™, you have to rely on risky zero-day reactive mitigation capabilities.
RADAR™ assists organizations in achieving, maintaining, and verifying the continuous closing of their DDoS vulnerability gaps. Reducing and maintaining the vulnerability level from an average of 48% to under 2% is ongoing.
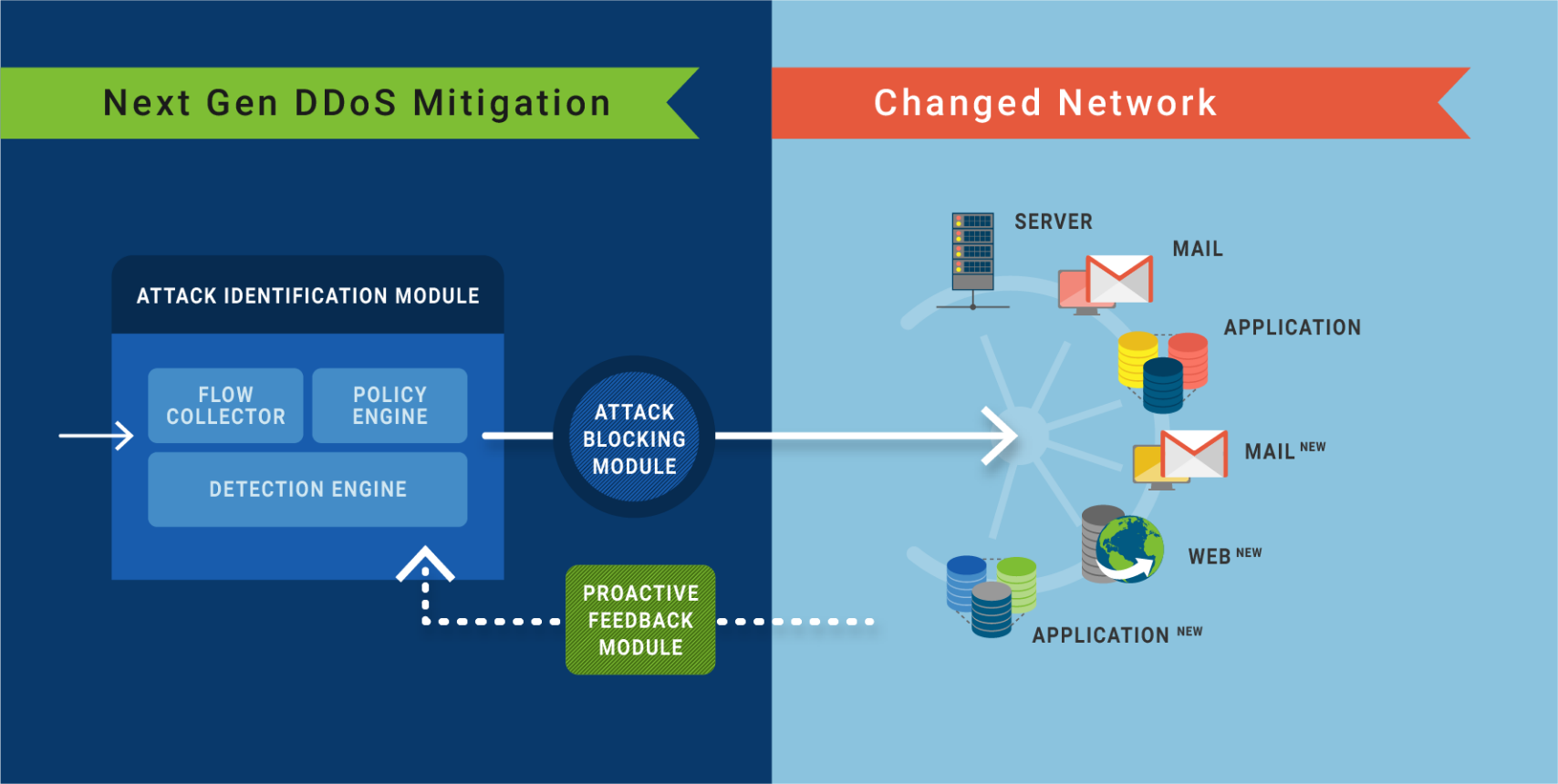
24/7 ongoing visibility into changing products and services network