The past weeks have seen a number of cybercriminal events that are noteworthy in that they give us a glimpse of where cybercrime in general and DDoS attacks in particular are heading. In this post we take a look at the forces driving DDoS attacks, put recent events in perspective, and assist in understanding what can be done about them.
The same way dynamite won’t detonate without a blast cap, networks of slaved computing devices (botnets) cannot unleash distributed denial of service (DDoS) attacks without command & control (C&C) programs to orchestrate the attack. The recent events are impacting these two essential components of DDoS attacks: Botnets and their C&C programs in a way that is transforming the threat of DDoS attacks.
Lowering the bar, and Leapfrogging over it
As depicted in Figure 1 below, the number of devices connected to the internet, the “Internet of Things“ (IoT), such as: webcams, routers, CCTVs, traffic lights, smart home appliances and the like, is growing exponentially and is estimated to reach approximately 50 Billion devices by 2020.
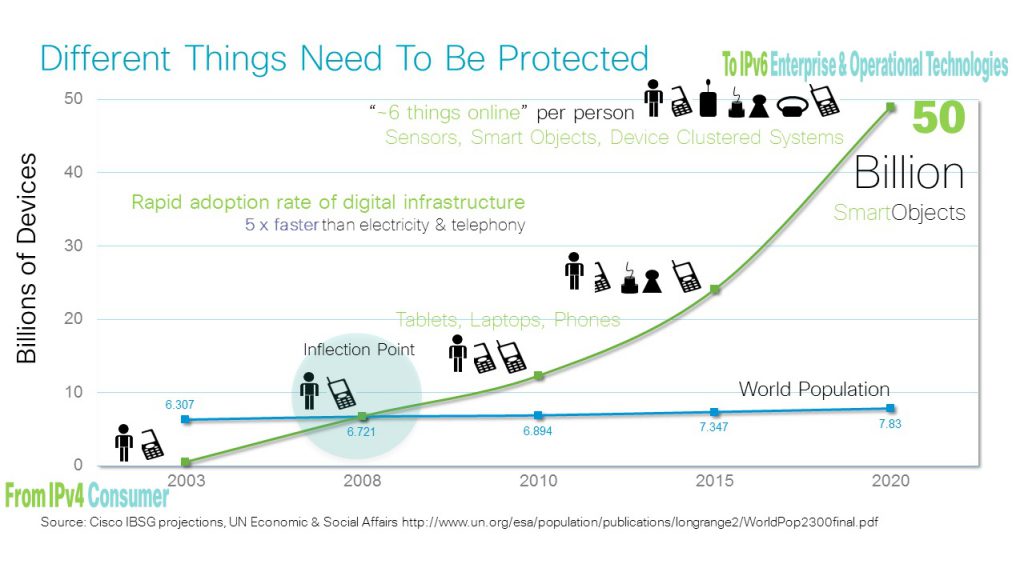 Figure 1: Growth in IoT Devices, Source: Cisco IBSG, April 2011
Figure 1: Growth in IoT Devices, Source: Cisco IBSG, April 2011
The reason IoT devices are attracting cybercriminals’ attention is that the overwhelming majority of them are surprisingly simple to compromise. As Alexandra Gheorghe from Bitdefender summarizes it “[IOT Devices are] constrained in memory and computer resources, can’t always support complex and evolving security algorithms. They don’t include long-term support or automatic firmware updates despite being created with longevity in mind. And most devices are, to the end user, like black boxes.” (For more from Alexandra Gheorghe on this see: The IoT is the Internet of Easy Home Hacking).
With literally billions of these devices coming online every year, cybercriminals will be able to harvest increasingly large botnets from which to unleash malicious attacks. The September DDoS assaults against Krebsonsecurity and then OVH the French ISP are noteworthy because they were found to both use botnets of such IoT devices that generated attacks at rarely seen magnitudes.
Now, you might be thinking that having these billions of unsecured devices out there is one thing, but compromising them and controlling them as a coordinated botnet takes a level of sophistication and resources which are neither trivial nor readily available to just anyone.
Well, you’d be wrong.
IoT, we have a problem!
As if the two massive attacks against Krebsonsecurity and OVH weren’t enough for one month, by the time September had ended cybercriminals had disseminated the source code (named “Mirai“) used to generate the attack on Krebsonsecurity – making it available for anyone. For free.
Mirai is designed to scan the internet for devices and automatically attempt to hack them using common default username and password combinations. This, as Krebs noted:
“virtually guaranteeing that the Internet will soon be flooded with attacks from many new botnets powered by insecure routers, IP cameras, digital video recorders and other easily hackable devices.”
The European Commission, was quick to respond and will be proposing new legislation designed to improve the security of the IoT devices they manufacture. Others may follow, but however useful these changes are, they will no doubt take time and in the meanwhile cybercriminals can be expected to unleash a new era of DDoS activity.
What can be done?
There are two aspects that need to be addressed when evaluating the implications of this new age of DDoS attacks: The Quantitative and Qualitative.
By quantitative, we mean the volume of traffic Internet Service Providers (ISPs) make available to each customer (or web site), also known as ‘Pipe Bandwidth’. No matter how powerful a site’s DDoS mitigation posture is, if a site’s pipe bandwidth is saturated it will cease functioning. The expected increase in the size of ISP DDoS attacks will mean that ISPs need to scale up on the bandwidth they provide their customers to ensure attacks do not exceed the allocated bandwidth and ‘choke’ customers’ websites.
By qualitative, we mean the different types of DDoS attacks being launched (i.e. Layer 3, Layer 4 or Layer 7 / Application layer attacks). For News, journalist, human rights, and election monitoring sites that do not have the resources to pay for DDoS mitigation, Google’s Project Shield, offers a free service that uses Google technology to protect news sites and free expression from DDoS attacks on the web.
For companies who do have DDoS mitigation either cloud-based or on premise devices, the only way to know their sites and online services are safe from DDoS attacks is by actively and regularly assessing their DDoS mitigation posture. This involves sessions of controlled simulations that not only identify vulnerabilities in deployed and cloud based DDoS mitigation systems – well before cybercriminals do – but also allows teams to verify their processes and procedures are adequate.


