Overview
With all the recent hype on “NTP DDoS” attacks, I took some time to understand why this attack became so popular. After researching the attack and the viability of the attack from the attacker’s perspective, I saw quickly why this vector is becoming the new “DNS” DDoS attack. Simply put, it’s extremely easy to cultivate and utilize NTPD resources worldwide.
Similar to DNS attacks, NTP DDoS attacks give the attacker the ability to perform “Guerrilla Cyber Warfare” style attacks. Hit quickly, hit hard, and be gone!
The unsuspecting victim never knows where it came from and by the time you start to get a grasp on the situation, all returns to normal.
Similarities to another asynchronous DDoS attack
Both DNS and NTP have in common the fact they both use asynchronous communication and have a great amplification metric. For instance, in my demo, I show an example of an NTP daemon that can be queried by anyone on the WWW, and how easy it was to get an amplification value of 350+ times my original request. That is what makes this attack very attractive for attackers.
With DNS attacks you have to find authoritative servers that will respond at a high rate to “ANY” type queries and then you have a node in your BOT for attacking. Though there are still many such DNS servers you can use to exploit in an asynchronous DDoS attack, there’s nothing like a new weapon for those wanting to get the biggest volumetric attacks possible.
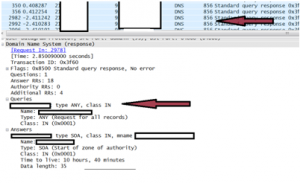
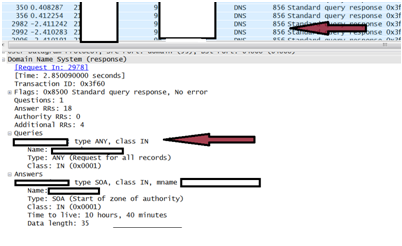
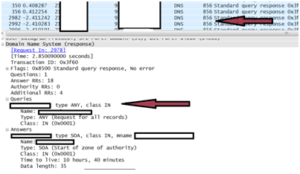
Illustration of “ANY” DNS response Attack (Reflective/Amplified)
*The Illustration below shows a small “ANY” RR request is made (In this case 82 bytes) to the participating DNS server (With the spoofed victim SRC IP).
*The victim receives a packet in the response of 856 bytes. More than 10 times the size of the original request.
From the above, we can see the amplification vector of DNS is nowhere near the same “bang for your buck” as the NTP amplification attack metric.
NTP DDoS Attack Analysis Demo
The above demo demonstrates how the NTP DDoS attack is technically possible. It’s structured as follows:
- Overview of the NTP Protocol.
- Reflective and Amplified DDoS attacks.
- NTP Attack demo – How the attack works.
- Mitigation options.
Mitigation
NTP attack traffic is actually easier to mitigate than DNS attack traffic since NTP’s actual traffic rate should never be anywhere near that of DNS traffic rates, this is simply because both protocols are very different in their practical uses. DNS also has a few attack flavors which mingle well with your ordinary traffic, making it tougher to mitigate without false positives. Behavioral systems will identify attack traffic from legit traffic pretty quickly with an ongoing NTP attack. Having said that, the sheer volume of the recent attacks reported by multiple vendors is between 300-500Gbit/s of traffic, that’s the main challenge.
How this vector be mitigated
Networks don’t have anywhere near the bandwidth to sustain an onslaught of attacks of 300-500Gbit/s and will be forced to go through a scrubbing center if they find themselves the target of such a volumetric attack.
Near the end of the demo I mention some reasons why you need to still retain CPE equipment to fight DDoS attacks, this mainly applies to larger organizations though.
Make sure you verify your mitigation strategy if you are a real-time sensitive network or website. I have seen in the past, many very large organizations, including governments, stock exchanges, and large eCommerce sites having outages over prolonged periods of time causing severe financial loss and credibility issues (Even after they paid for mitigation services).
Conclusions
Some organizations have “DDoS mitigation” systems in place but are taken by surprise when they have extended outages. This is because they haven’t fully tested their systems under a well-coordinated DDoS attack scenario (Or maybe thought some minimal tests would suffice). Those that perform automatic, continuous DDoS testing across the entire DDoS attack surface will survive an attack campaign without any major disruptions, from the start of the campaign. In the same way networks cannot have security verified without a pentest no DDoS mitigation system can be verified without full visibility into an organization’s dynamic attack surface.