The DDoS mitigation industry is scaling up capacity following a consistent increase in the number of DDoS attacks and recent indications that IoT-based DDoS attacks are expected to grow significantly.
The DDoS attack vector continues to wreak havoc in 2017, with a reported 380% spike in the number of DDoS attacks identified in Q1, compared to the same period last year. A recent study shows a year on year increase of 220% (see graph) in the number of different types of malware designed to hijack IoT devices.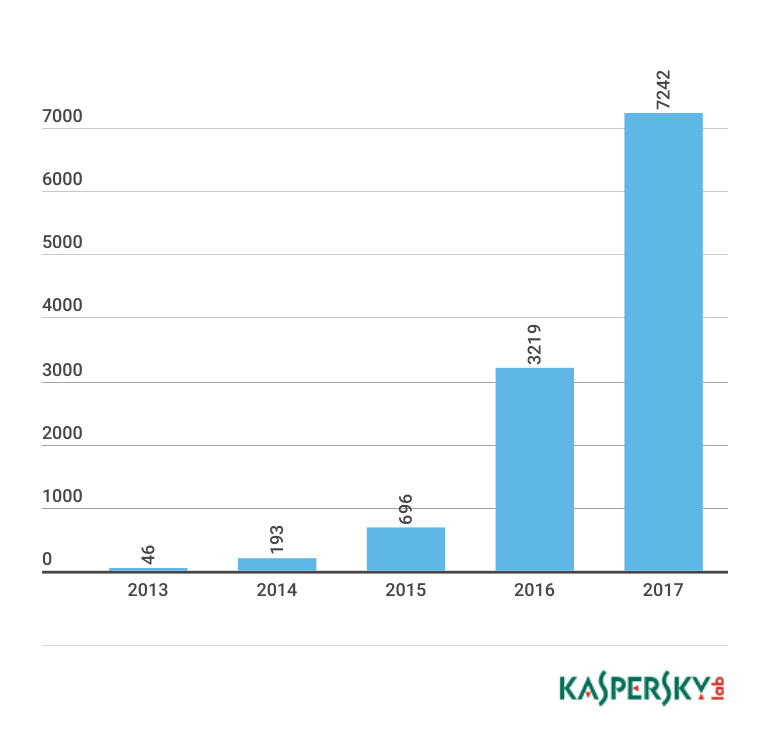
DDoS Mitigation providers are taking heed, with Arbor dedicated to quadrupling their capacity to 8Tbps by the end of 2017, and both Neustar Security Solutions and OVH committing to capacities of over 10Tbps.
A DDoS mitigation Gap occurs whenever DDoS traffic bypasses a company’s DDoS mitigation defenses, and penetrates the target network.
The reasons for such gaps vary from some types of DDoS attacks that are completely unnoticed by DDoS mitigation, to a range of configuration issues that let through traffic that should be mitigated.
However the problem is that visibility of DDoS mitigation gaps is currently nonexistent to those cybersecurity practitioners who are responsible for production uptime.
Companies do not know how well their mitigation is performing, or where their configuration problems are, leaving them and their vendors to troubleshoot issues at the very worst possible time, that is, when systems are down at the height of a DDoS attack.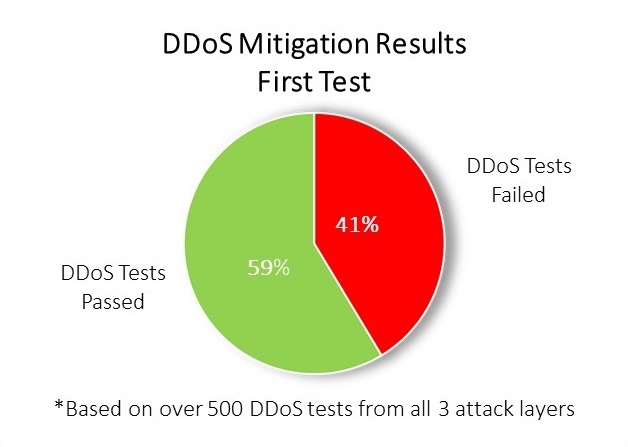
Results from over 500 hundred DDoS tests run by MazeBolt on companies from a wide range of industries, shows that on their first test, companies failed 41% (on average) of DDoS tests – simulations of real DDoS attacks conducted in a highly controlled manner to help companies understand their mitigation gap so they can strengthen their mitigation proactively.
This means that after a company has deployed their DDoS mitigation strategy, on average it will stop only six out of ten attacks.
To solve this, with insight about where their DDoS mitigation posture was leaking, companies could go back to vendors to reconfigure settings and harden their DDoS mitigation posture.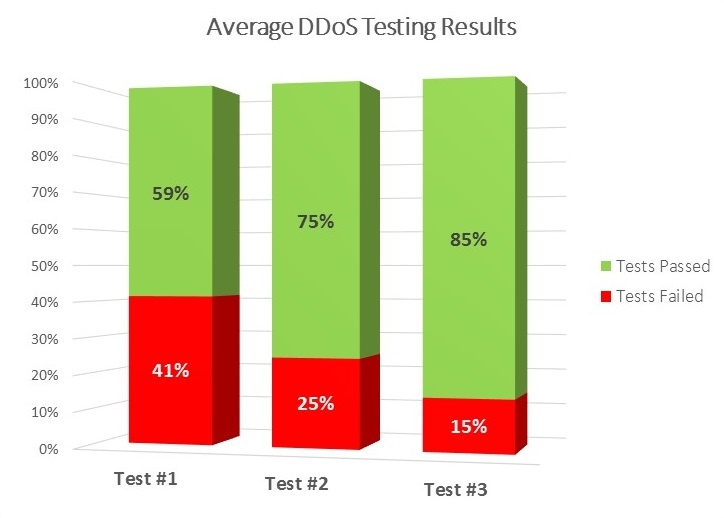
As depicted in the graph by repeating the testing only three times, companies were able to reduce their mitigation gap from an average of 41% in the first test to an average of 25% in the second and only 15% in the third – reflecting a 65% strengthening of their DDoS mitigation.
Paraphrasing Heraclitus one might say you can never test the same DDoS mitigation twice, but our data clearly shows that testing it three times will strengthen it considerably.