Introduction
Continuous Threat Exposure Management (CTEM) is one of the top technology trends according to Gartner, Inc., a leading research and advisory firm in the technology space dedicated to helping businesses around the globe make critical IT decisions. CTEM is an innovative, realtime framework designed to address the evolving landscape of cybersecurity threats. As organizations increasingly face ever-more-sophisticated attacks, including a growing number of Distributed Denial-of-Service (DDoS) attacks, traditional vulnerability management techniques fall short.
DDoS attacks are a critical area of concern for security leaders in today’s digital ecosystem. DDoS attacks are increasing at an unprecedented rate, and pose a growing threat to organizations in a wide variety of sectors. Researchers noted 50 percent more DDoS attacks were launched by threat actors during the first quarter of 2024 over the same period last year, with thwarted DDoS attacks increasing by 93 percent year-over-year. DDoS attacks disrupt business continuity, and they can result in significant financial losses, regulatory scrutiny, and reputational harm.
CTEM offers a proactive and continuous framework that can be used to identify, evaluate, and mitigate DDoS vulnerabilities before they can be exploited. This eBook explores how to leverage CTEM specifically to reduce the risk of DDoS attacks – ensuring the business continuity of your organization’s online services and improving resilience.
What is CTEM?
CTEM represents a refreshing, new approach to cybersecurity resilience, moving from reactive to proactive threat management. Unlike traditional methods that rely on periodic assessments, CTEM involves continuous monitoring and real-time response.

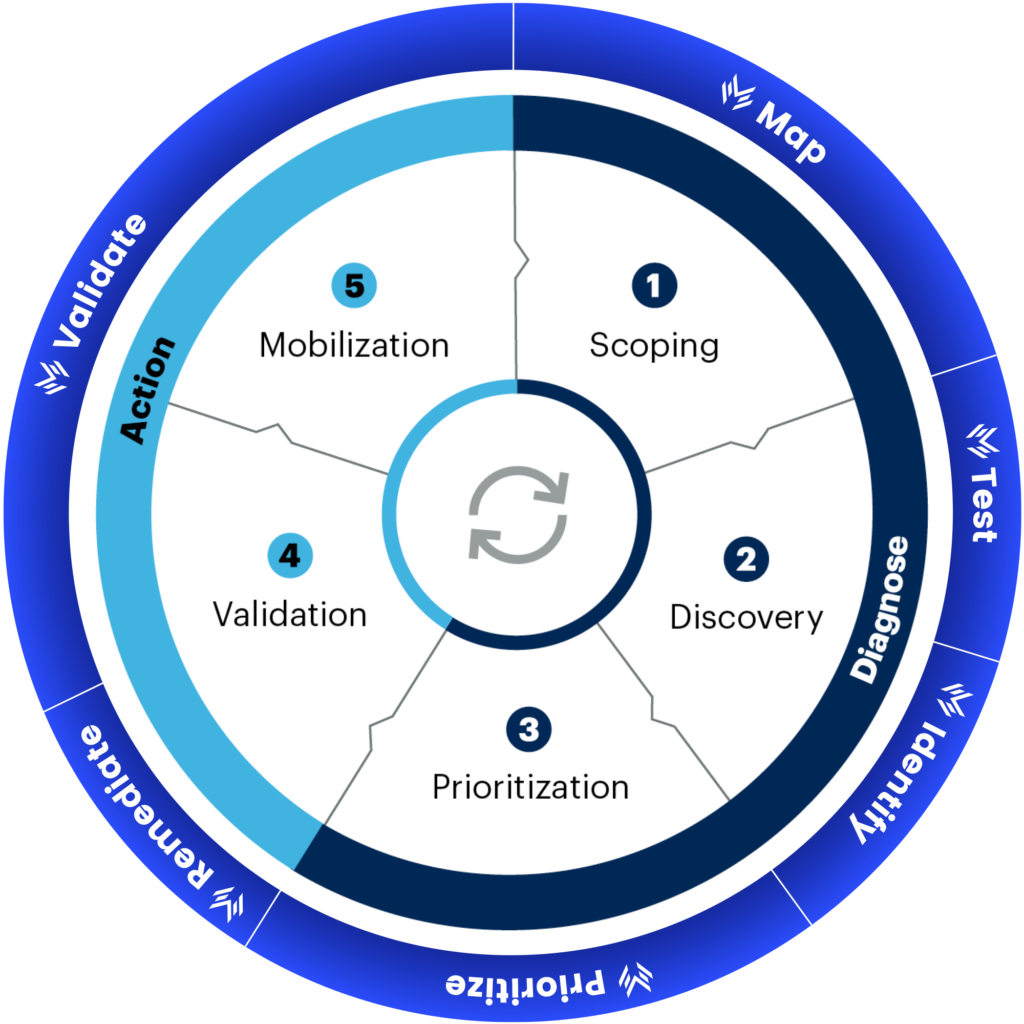
The CTEM program is a continuous cycle – with 3 diagnostic steps and 2 active steps:
- Scoping: Identify and map the entire attack surface of the organization. This includes all digital assets and potential entry points for threats.
- Discovery: Continuously monitor and uncover vulnerabilities, misconfigurations, and other security gaps across all environments, including on-prem, cloud, and IoT.
- Prioritization: Assess and prioritize threats based on their potential impact on the business. This ensures that the most critical vulnerabilities are addressed first.
- Validation: Regularly test the effectiveness of security controls and the organization’s ability to respond to identified threats. This includes simulated attacks, automated testing, and remediation.
- Mobilization: Implement and enforce security measures, ensuring that security teams are prepared to respond to threats quickly. This involves training, process improvements, and leveraging security tools to reduce obstacles
Validate Your DDoS Protections with a Proactive Approach
Traditional DDoS Red Team testing focuses on identifying and patching known vulnerabilities through periodic scans. However, this approach often leads to delays in addressing new threats and lacks integration with other security tools.
CTEM, on the other hand, offers several advantages:
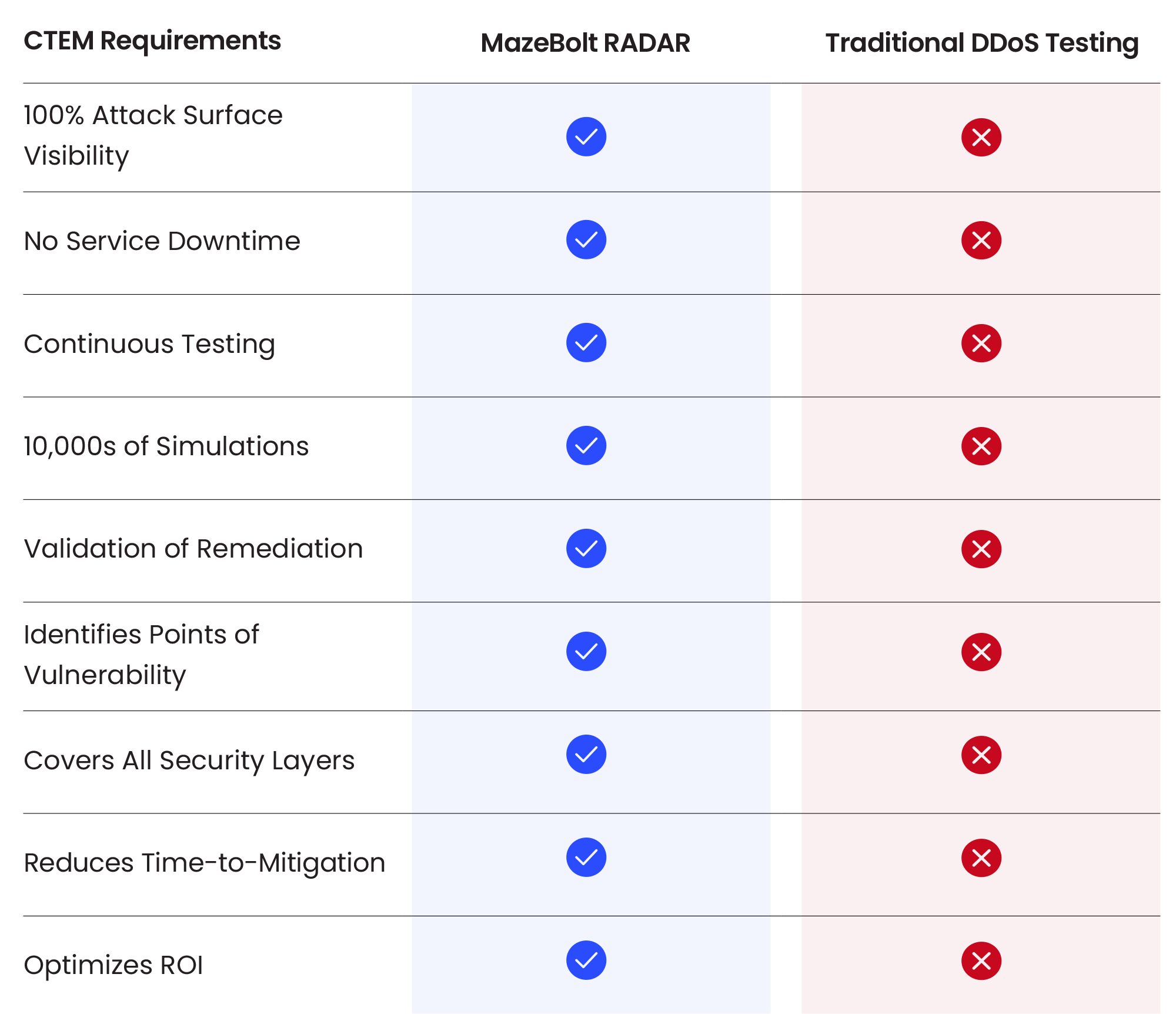
| Real-Time Detection | CTEM recommends continuous scanning and real-time detection of vulnerabilities, reducing the window of exposure. |
| Comprehensive Coverage | Unlike traditional methods, CTEM covers all assets, including mobile, IoT, and cloud environments. |
| Risk-Based Prioritization | CTEM relates to vulnerabilities based on their potential business impact, not just severity, ensuring that critical threats are addressed first. |
| Integration and Automation | CTEM integrates with existing security tools and automates detection, prioritization, and remediation processes, enhancing overall efficiency. |
| Enhanced Reporting | CTEM provides advanced reporting and visualization tools, helping organizations understand threats and communicate risks effectively to stakeholders and meet compliance requirements. |
CTEM goes beyond the scope of traditional vulnerability management with a proactive, risk-based strategy that covers all sources of threat exposures, including misconfigurations, open ports, and weak encryption. It provides real-time detection of new vulnerabilities through comprehensive, ongoing monitoring of the entire IT plant.
Enterprises Continue to be Highly Vulnerable to DDoS
Despite the many technological developments in the field of cybersecurity, DDoS attacks continue to be a significant issue. According to recent reports, the surge in DDoS attacks this year is unprecedented in rate and scope.
Although enterprises typically deploy DDoS protections, attacks are still causing damage across a variety of sectors and have the ability to overwhelm a network, disrupt services, and cause financial damage.
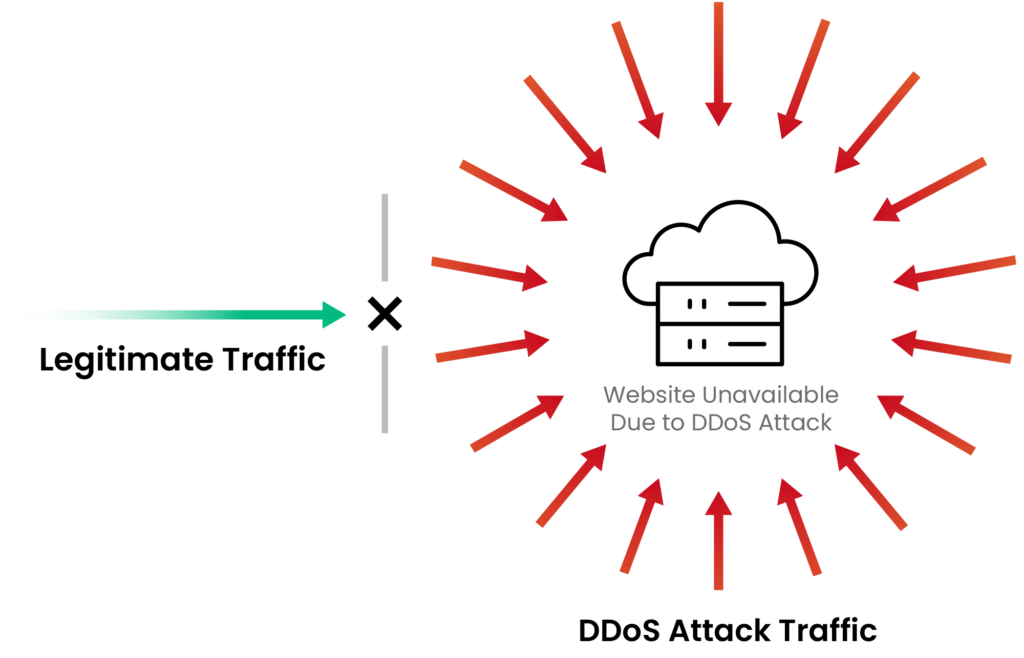
These attacks cause damage, as seen in the recent attack on Google (which saw 400 million requests per second) and on Microsoft Azure. Due to their sheer volume and sophistication, DDoS attacks are
hitting enterprises across sectors including government institutions, the banking and financial services industry, and more.
Checking and testing how your deployed DDoS protection solutions are configured and proactively identifying misconfigurations (so they can be addressed) can improve resilience by about 20% – significantly reducing the risk of DDoS attack and providing better protection against potential disruptions.
Move to Proactive DDoS Vulnerability Simulation
What makes CTEM particularly attractive is that existing tools and processes can be leveraged as a starting point for a CTEM program.
Implementing CTEM requires adopting a shift in mindset from reactive to proactive DDoS Vulnerability Testing. Part of CTEM implementation involves deciding what needs to be fixed – and what can be incorporated as-is based on outcome-driven, business-tuned metrics.
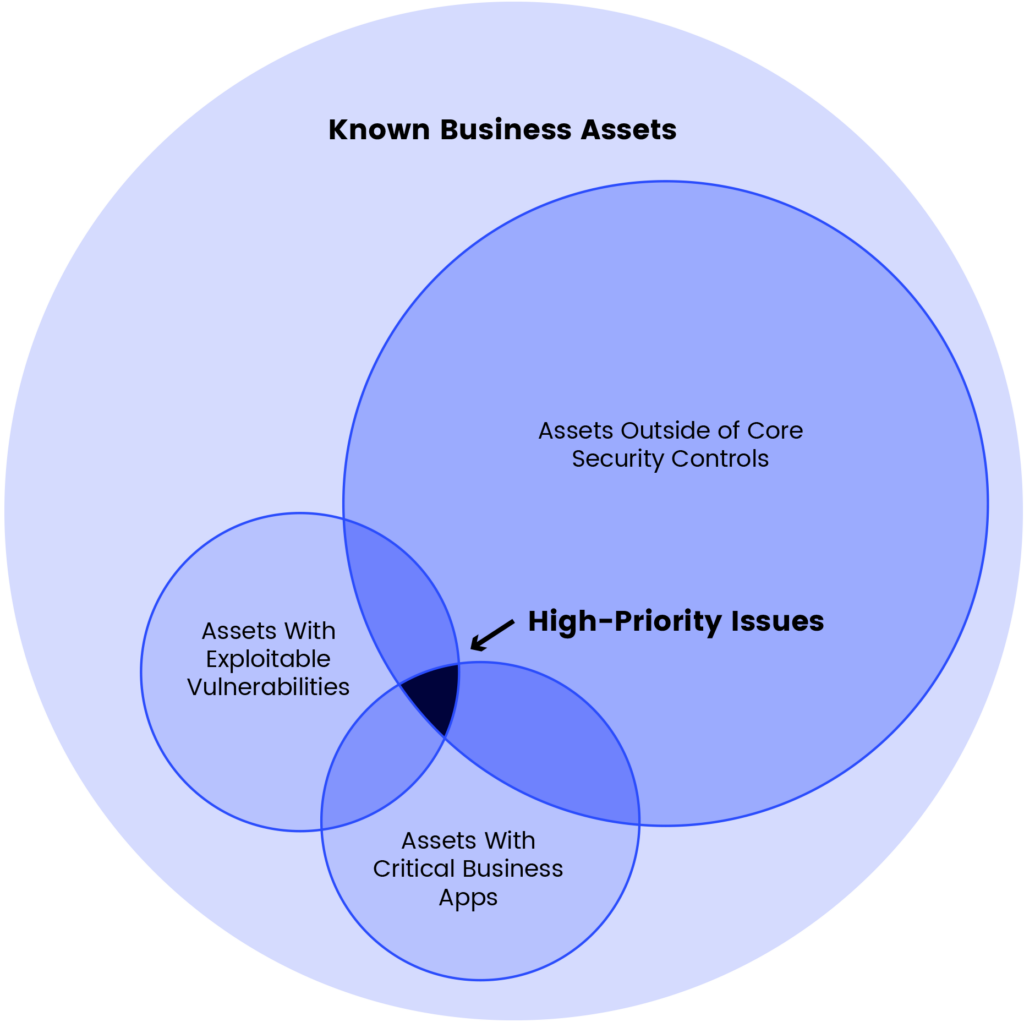
Eliminating all vulnerabilities is impossible. As a result, identifying the different kinds of DDoS vulnerabilities and evaluating which ones pose the greatest danger to the business is a crucial part of the process. The most critical DDoS vulnerabilities are going to appear where you see an overlap of:
- Assets with exploitable vulnerabilities
- Assets with critical business apps
- Assets outside of core security controls
A key aspect of the CTEM process involves aligning with leadership teams to establish how exposure should be reported – by using existing risk assessments to anchor the conversation, and by defining a consistent and agreed categorization of discoveries. As Gartner states, “The most valuable outputs of a continuous threat exposure management (CTEM) process are the recording and reporting of potential impact to risk reduction and justification of organizational value.” This is particularly important because regulatory requirements are becoming stricter with audit cycles and potential fines, as highlighted in:
Continuous DDoS Attack Testing Is Key to Eliminating Risk
Even with the best DDoS mitigation solutions in place, organizations typically suffer up to 75 percent exposure of their DDoS attack surface. That’s partly because DDoS protection solutions initiate testing only periodically (typically, a few times a year), and tend to test a very limited percentage of an organization’s attack surface.
What is more effective in reducing the risk of DDoS attack is a continuous, non-disruptive strategy that is aligned
with the proactive CTEM approach. And that’s where MazeBolt RADAR comes in – supporting CTEM adoption by providing a comprehensive solution for DDoS Vulnerability Management that addresses all 5 steps of the CTEM framework. It offers continuous monitoring of DDoS protection solutions and real-time threat detection, ensuring that organizations are always aware of potential DDoS vulnerabilities.
The following table illustrates how MazeBolt RADAR compares to traditional DDoS testing tools, in the implementation of the CTEM approach for DDoS attack testing and simulation
Key Takeaways
Gartner’s CTEM strategy is an important framework that can help your organization proactively identify and eliminate DDoS vulnerabilities by prioritizing and managing vulnerability remediation. Using the CTEM approach, MazeBolt helps organizations improve cyber resilience and reduce the risk of DDoS attack through:
- Proactive Approach
CTEM shifts the focus from reactive to proactive of DDoS Vulnerability Management, ensuring continuous monitoring and real-time response to threats - Comprehensive Coverage
CTEM covers all digital assets, including IT, could and IoT environment, providing a holistic view of the DDoS attack surface. - Risk-Based Prioritization
Prioritized DDoS threats based on their potential business impacts ensures that critical vulnerabilities are addressed first.
- Integration and Automation
Seamless integration with existing security tools and automation of processes enhance overall efficiency and effectiveness - DDoS Protection Alignment
MazeBolt RADAR provides continuous monitoring of DDoS protection solutions, real-time DDoS threat detection, and advanced reporting – helping organizations reduce the risk of DDoS attack.